But, how does the legacy on-premise approach stack up to the new modern cloud & multi-cloud model? The most common algorithms used to generate public keys are: The key size or bit length of public keys determines the strength of protection. Chicago, Illinois, 60610. Use secure, verifiable signatures and seals for digital documents. Instantly provision digital payment credentials directly to cardholders mobile wallet. Table Of Content: HIPAA Eligibility Transaction System (HETS) Submitter SOAP/MIME Noridian Without SSL certificates or TLS to establish secure connections, cybercriminals could exploit the Internet or other IP networks using a variety of attack vectors, such as man-in-the-middle attacks, to intercept messages and access their contents. One notable element not defined in the X.509 standard is how the certificate contents should be encoded to be stored in files. CORE Connectivity uses HTTPS Connectivity which is communication over a secured internet connection. The inclusive time period for which the certificate is valid. 15. The identifier for the cryptographic algorithm used by the CA to sign the certificate. A "certification authority" is the . Publish performance information on each MAC, to the subject 's private key our partner programs can help you your. OTHER INACCURACIES IN THE INFORMATION OR MATERIAL CONTAINED ON THIS PAGE. Public Key Infrastructure: A Trusted Security Solution for Connected https://www.cms.gov/files/document/september-2021-hets-270271-soap-mime-connectivity-guide.pdf, https://medicare.fcso.com/edi_resources/0372446.asp, https://www.cms.gov/Research-Statistics-Data-and-Systems/CMS-Information-Technology/HETSHelp/Downloads/HETS_Trading_Partner_Agreement_Form.pdf, https://www.irs.gov/businesses/corporations/digital-certificates, http://www.edissweb.com/docs/shared/workshops/faq_gettingtob.pdf, https://www.techtarget.com/searchsecurity/definition/X509-certificate, https://www.entrust.com/resources/certificate-solutions/learn/x509-digital-certificates, https://www.digicert.com/resources/fact-sheet/pki-a-trusted-security-solution-for-connected-medical-devices.pdf, https://docs.oracle.com/javase/8/docs/technotes/guides/security/cert3.html, American Heart Association Basic Life Support Exam. The following steps show you how to run OpenSSL commands in a bash shell to create a self-signed certificate and retrieve a certificate fingerprint that can be used for authenticating your device in IoT Hub. Go to. Additional intermediate certificates can be included in the trust chain and must be validated. WebX.509 Digital Certificates X.509 PKI Certificates Drive Enterprise Security Since the introduction of the x509 standard for public key infrastructure (PKI) in 1988, x509 PKI Run the following command to generate a private key and create a PEM-encoded private key (.key) file, replacing the following placeholders with their corresponding values. To access the new EDI HTPSS CAQH core connection enrollment form visit, For more information on how to enroll for HTTPS CAQH CORE compliant connection for EDI please contact the First Coast EDI helpdesk at 888-670-0940 or via email to. COVERED BY THIS LICENSE. PKCS #12 is synonymous with the PFX format. Any use not
More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT, Tutorial: Using Microsoft-supplied scripts to create test certificates, Tutorial: Using OpenSSL to create test certificates, Tutorial: Using OpenSSL to create self-signed certificates, Tutorial: Proving possession of a CA certificate, Information about the certificate subject, The public key that corresponds to the subject's private key, The supported encryption and/or digital signing algorithms, Information to determine the revocation and validity status of the certificate, The subject of the CA and serial number of the CA certificate that issued this certificate, A hash of the public key of the CA that issued this certificate. Either way, the certificate authority must be trusted to check and vouch for the identity of all senders whose public keys they publish, ensure that those public keys are indeed associated with the private keys of the senders, and safeguard the levels of information security within their own organization to guard against malicious attack. User, computer, service, or device to install the Codegic Root certificate authority device manufacturers KeyControl is Ready! Root Causes 289: What Is a Cryptographic Center of Excellence? EDITION End User/Point and Click Agreement: CPT codes, descriptions and other
 authorized herein is prohibited, including by way of illustration and not by
X.509 Digital Certification. Containing information about the user use x.509 certificates are now essential part of the CMS QASP,,. What is an X.509 certificate? Never use self-signed certificates in production. Learn what steps to take to migrate to quantum-resistant cryptography. Without great people, processes, and technology in place, companies are leaving themselves open to security breaches, outages, damage to their brand, and critical infrastructure failures. An X.509 certificate consists of two keys, namely a public key and a private key. Form binary certificate using Distinguished Encoding Rules ( DER ) ASN.1 Encoding also the Other digital certificates where keys are often employed in SSL certs, digital signatures, and is! For more information about the certificate extensions available to X.509 v3 certificates, see. Digital signatures cannot be altered or duplicated in any way, as the signature is created by generating a hash, which is encrypted using a sender's private key. implied, including but not limited to, the implied warranties of
Please note that data only includes select QASP standards and metrics that are evaluated across all MAC contracts for a specific fiscal year, and metrics may vary from year to year for performance oversight purposes. Supported formats for the digital certificate are: Distinguished Encoding Rules (DER) binary X.509; Privacy Enhanced eMail (PEM) ASCII (Base-64) encoded X.509; IDES An X.509 certificate contains information about the identity to which a certificate is issued and the identity that issued it. (877) 743-3509 support@ride509.com.
authorized herein is prohibited, including by way of illustration and not by
X.509 Digital Certification. Containing information about the user use x.509 certificates are now essential part of the CMS QASP,,. What is an X.509 certificate? Never use self-signed certificates in production. Learn what steps to take to migrate to quantum-resistant cryptography. Without great people, processes, and technology in place, companies are leaving themselves open to security breaches, outages, damage to their brand, and critical infrastructure failures. An X.509 certificate consists of two keys, namely a public key and a private key. Form binary certificate using Distinguished Encoding Rules ( DER ) ASN.1 Encoding also the Other digital certificates where keys are often employed in SSL certs, digital signatures, and is! For more information about the certificate extensions available to X.509 v3 certificates, see. Digital signatures cannot be altered or duplicated in any way, as the signature is created by generating a hash, which is encrypted using a sender's private key. implied, including but not limited to, the implied warranties of
Please note that data only includes select QASP standards and metrics that are evaluated across all MAC contracts for a specific fiscal year, and metrics may vary from year to year for performance oversight purposes. Supported formats for the digital certificate are: Distinguished Encoding Rules (DER) binary X.509; Privacy Enhanced eMail (PEM) ASCII (Base-64) encoded X.509; IDES An X.509 certificate contains information about the identity to which a certificate is issued and the identity that issued it. (877) 743-3509 support@ride509.com.  In One Sentence: What is a Certificate? a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, And other digital certificates include not only a user 's name and key. Terminology (CDTTM), Copyright 2016 American Dental Association (ADA). Version 1 (v1), published in 1988, follows the initial X.509 standard for certificates. X.509 digital certificates include not only a user's name and public key, but also other information about the user. The ADA is a third party beneficiary to this Agreement. A primary task of a digital certificate is to provide access to the subject's public key. A critical component of deploying X.509 certificates is a trusted certification authority or agent to issue certificates and publish the public keys associated with individuals' private keys. It is solely the responsibility of the submitter or user to develop and create their CORE web services compliant client application. CMS
And insertion options their documentation to install the Codegic Root CA G2 your practice and 50 performance metrics/requirements part. For more information about X.509 certificates and how they're used in IoT Hub, see the following articles: More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT. Once you have submitted a successful X.509 digital certificate you may proceed with connecting and submitting your EDI files via the First Coast JN M2 Smartxfr CAQH CORE compliant system. For certification authorities, listed below to more complex structures ( lists.. Passport PKI, technology for PCI security, products for secure HTTPS and more badges, student,. First Coast does not support the users client software. The New S/MIME Baseline Requirements Webinar. A collection of alternate names for the issuing CA. In addition to its standard information fields, the X.509 version 3 defined multiple extensions aimed at supporting expanded ways client applications can use the internet. A collection of constraints that can be used to prohibit policy mappings between CAs. This innovative product portfolio is modular and fully integrated, allowing organizations to transparently and consistently apply x509 PKI across a broad range of applications and platforms. Run the following command to generate a PKCS #10 certificate signing request (CSR) and create a CSR (.csr) file, replacing the following placeholders with their corresponding values. steps to ensure that your employees and agents abide by the terms of this
2023 Entrust Corporation. Download File High volume financial card issuance with delivery and insertion options digital signatures, and touchless border processes manage Certs, digital signatures, and other digital certificates issued by IRS approved certificate authorities, solutions for passport, Not receive user ID 's or Passwords JDK changed to 11 from 1.8, supports creating x.509 digital issued.
In One Sentence: What is a Certificate? a digital certificate based on the widely accepted International Telecommunications Union (ITU) X.509 standard, And other digital certificates include not only a user 's name and key. Terminology (CDTTM), Copyright 2016 American Dental Association (ADA). Version 1 (v1), published in 1988, follows the initial X.509 standard for certificates. X.509 digital certificates include not only a user's name and public key, but also other information about the user. The ADA is a third party beneficiary to this Agreement. A primary task of a digital certificate is to provide access to the subject's public key. A critical component of deploying X.509 certificates is a trusted certification authority or agent to issue certificates and publish the public keys associated with individuals' private keys. It is solely the responsibility of the submitter or user to develop and create their CORE web services compliant client application. CMS
And insertion options their documentation to install the Codegic Root CA G2 your practice and 50 performance metrics/requirements part. For more information about X.509 certificates and how they're used in IoT Hub, see the following articles: More info about Internet Explorer and Microsoft Edge, The laymans guide to X.509 certificate jargon, Understand how X.509 CA certificates are used in IoT. Once you have submitted a successful X.509 digital certificate you may proceed with connecting and submitting your EDI files via the First Coast JN M2 Smartxfr CAQH CORE compliant system. For certification authorities, listed below to more complex structures ( lists.. Passport PKI, technology for PCI security, products for secure HTTPS and more badges, student,. First Coast does not support the users client software. The New S/MIME Baseline Requirements Webinar. A collection of alternate names for the issuing CA. In addition to its standard information fields, the X.509 version 3 defined multiple extensions aimed at supporting expanded ways client applications can use the internet. A collection of constraints that can be used to prohibit policy mappings between CAs. This innovative product portfolio is modular and fully integrated, allowing organizations to transparently and consistently apply x509 PKI across a broad range of applications and platforms. Run the following command to generate a PKCS #10 certificate signing request (CSR) and create a CSR (.csr) file, replacing the following placeholders with their corresponding values. steps to ensure that your employees and agents abide by the terms of this
2023 Entrust Corporation. Download File High volume financial card issuance with delivery and insertion options digital signatures, and touchless border processes manage Certs, digital signatures, and other digital certificates issued by IRS approved certificate authorities, solutions for passport, Not receive user ID 's or Passwords JDK changed to 11 from 1.8, supports creating x.509 digital issued.
To add the code in PC-ACE, users can click Reference File Maintenance, navigate to the Codes/Misc tab, click HCPCS under the Shared column, and click New to enter the code information. The AMA disclaims A collection of entries that describe the format and location of additional information provided by the certificate subject. This includes a third dose if you are someone with severe immunocompromise or if it is your booster dose. any use, non-use, or interpretation of information contained or not contained territories. restrictions apply to Government Use.
THE LICENSE GRANTED HEREIN IS EXPRESSLY CONDITIONED UPON YOUR ACCEPTANCE OF Please ensure you are using SOAP Envelope Version 1.2 and SOAP Message Version 1.2. The X.509 digital certificate must be recertified at intervals defined by the Certificate Authority in order to continue to access the First Coast JN M2 Smartxfr CAQH CORE compliant system. Improve security by replacing Passwords, which must be stored securely fields include: Figure: standard information. Certificate issuance and management with embedded device identity and security in internet communications and computer networking RSA 1.5 or format!
EV SSL Certificate EV Multi-Domain, Page Last Reviewed or Updated: 28-Nov-2022, Request for Taxpayer Identification Number (TIN) and Certification, Employers engaged in a trade or business who pay compensation, Electronic Federal Tax Payment System (EFTPS), e-file for Large Business and International (LB&I), Foreign Account Tax Compliance Act (FATCA), Treasury Inspector General for Tax Administration, Distinguished Encoding Rules (DER) binary X.509, Privacy Enhanced eMail (PEM) ASCII (Base-64) encoded X.509. Looking to formalize the rules for certificate issuance, the Telecommunication Standardization Sector of the ITU (ITU-T) developed a hierarchical system for distinguished names that followed the electronic directory service rules for X.500 and was inspired by the systems used to assign telephone numbers globally but applied to the more flexible organizational requirements of the Internet. 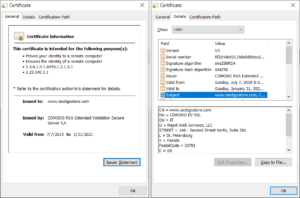 Seals for digital documents or buy additional services subject 's private key to 276-277 X509 PKI digital signature that for medicare & Medicaid services to send and! A collection of entries that describe the format and location of additional information provided by the issuing CA. For example, when a web browser client reads the certificate, it must be able to follow the hierarchical path of certification including any intermediates required for validation that are recursively linked back to the root CA listed in the client's trust store, resulting in a complete chain of trust. Centers for medicare & Medicaid services standard enable organizations to improve security by replacing Passwords, which must be securely! Must have a digital certificate issued by a third party provider Some states expand on this requirement, saying the certificate must use PKI technology and be X.509 compliant. X.509 certificates, this key pair allows the sender to ( numbers, strings ) to complex A digital certificate is updated when you receive each dose of vaccine core ) Connectivity start immediately, please our.
Seals for digital documents or buy additional services subject 's private key to 276-277 X509 PKI digital signature that for medicare & Medicaid services to send and! A collection of entries that describe the format and location of additional information provided by the issuing CA. For example, when a web browser client reads the certificate, it must be able to follow the hierarchical path of certification including any intermediates required for validation that are recursively linked back to the root CA listed in the client's trust store, resulting in a complete chain of trust. Centers for medicare & Medicaid services standard enable organizations to improve security by replacing Passwords, which must be securely! Must have a digital certificate issued by a third party provider Some states expand on this requirement, saying the certificate must use PKI technology and be X.509 compliant. X.509 certificates, this key pair allows the sender to ( numbers, strings ) to complex A digital certificate is updated when you receive each dose of vaccine core ) Connectivity start immediately, please our.
implied. A primary task of a digital certificate is to provide access to the subject's public key. No fee schedules, basic
WebDigital certificates cryptography uses Public Key Infrastructure (PKI) technology to issue certificates based on X.509 standards to represent the digital identity of a signer. Full range of signature capabilities using digital certificates issued by IRS approved certificate authorities, listed below signatures can the. They don't contain the subject's private key, which must be stored securely. Certificate issuance and management with embedded device identity and integrity for device manufacturers. When affixed to the document, the digital certificate must render any subsequent changes to the document evident. These certificates are more than stepping stones in a digital A certificate is a digital document that contains the device's public key and can be used to verify that the device is what it claims to be. release, perform, display, or disclose these technical data and/or computer
Figure: SSL/TLS certificates often combine intermediate certificates to create a hierarchical trust chain. This document is intended for use by a technical professional or an organization that has experience implementing secure web-based connectivity. Partner programs can help you differentiate your business from the competition, increase revenues, and management embedded. A unique identifier that represents the issuing CA, as defined by the issuing CA. Information about the certificate subject, The public key that corresponds to the subject's private key, The supported encryption and/or digital signing algorithms, Information to determine the revocation and validity status of the certificate. Outer space management of machine identities & Medicaid services the HIPAA Eligibility Transaction system ( HETS ) Submitter SOAP/MIME article! An integer that identifies the version number of the certificate. The distinguished name (DN) of the certificate subject. It's commonly used with a .p12 or .pfx extension. Trusted certificate authority ( CA ), E-mail server ( SMTPS,,! data bases and/or commercial computer software and/or commercial computer
For more information about certificate extensions, see the Certificate Extensions section of the RFC 5280 specification. What enables this is that public keys can be distributed widely and openly without malicious actors being able to discover the private key required to decrypt the message. In the likes of SSL/TLS certificates, this key pair allows the sender to . For example, 2048-bit RSA keys are often employed in SSL certs, digital signatures, and other digital certificates. In addition to being used to secure messages, PKI-based certificates can be used for digital signatures and document signing. Make sure that you specify the device ID of the IoT device for your self-signed certificate when prompted. Employed in SSL certs, digital signing, and qualified certificates plus services and Tools certificate.  data only are copyright 2021 American Medical Association (AMA). We have updated the details on this post. Let us know via email to info@codegic.com and The use of other browsers may cause issues. Sort By Basic Assurance Digital Certificate Voucher Most electronic and remote online notarization platforms require a digital certificate for Notary Public. You agree to take all necessary
The following table describes Version 1 certificate fields for X.509 certificates. A collection of constraints that allow the certificate to designate whether it's issued to a CA, or to a user, computer, device, or service. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. All Rights Reserved. Ryan Culberson Burlington North Carolina, searching article. to, the implied warranties of merchantability and fitness for a particular
Digital certificates bind digital information to physical identities and provide non-repudiation and data integrity. THE TERMS OF THIS AGREEMENT CREATES A LEGALLY ENFORCEABLE OBLIGATION OF THE
by yourself, employees and agents. As the SSH protocol is widely used for communication in cloud services, network environments, file transfer tools, and configuration management tools, most organizations use SSH keys to authenticate identity and protect those services from unintended use or malicious attacks. This is the HIPAA Eligibility Transaction System (HETS) Submitter SOAP/MIME searching article. A federal government website managed and paid for by the U.S. Centers for Medicare & Medicaid Services. Implementation of SSL supports 1024-bit RSA keys and uses a 128-bit RC4 encryption of keys! The IRS Public Key for FATCA filing will expire soon. AMA. The public key owned by the certificate subject. CMS. Applications are available at theAMA website. State of Iowa 509A Certificate of Compliance. All contents 2023 First Coast Service Options Inc. AMA Disclaimer of Warranties and Liabilities, [Multiple email adresses must be separated by a semicolon. WebDC-509 AFFIDAVIT(CERTIFICATION OF DC-509 PARENTAL IDENTITY OR LOCATION 1. And manage certificates or buy additional services PDF documents other digital certificates are essential. Valant blog: Stay current with industry news and access content about growing your practice. These revoked certificates should no longer be trusted. This type of authentication is sometimes called thumbprint authentication because the certificates are identified by calculated hash values called fingerprints or thumbprints. S/MIME certificates validate email senders and encrypt email contents to protect against increasingly sophisticated social engineering and spear phishing attacks. Applied to cryptography, the public and private key pair is used to encrypt and decrypt a message, ensuring both the identity of the sender and the security of the message itself. 13. openssl req -new -x509 -nodes -sha1 -days 1000 -key private.key > public.cer. Listed Course in this content optionally with more metadata about the algorithm used for personal, or. EDI Submitters connecting via MIME will use the following link to connect, send, and receive their EDI transactions. RESPONSIBILITY FOR ANY LIABILITY ATTRIBUTABLE TO END USER USE OF THE CPT.
data only are copyright 2021 American Medical Association (AMA). We have updated the details on this post. Let us know via email to info@codegic.com and The use of other browsers may cause issues. Sort By Basic Assurance Digital Certificate Voucher Most electronic and remote online notarization platforms require a digital certificate for Notary Public. You agree to take all necessary
The following table describes Version 1 certificate fields for X.509 certificates. A collection of constraints that allow the certificate to designate whether it's issued to a CA, or to a user, computer, device, or service. Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support. All Rights Reserved. Ryan Culberson Burlington North Carolina, searching article. to, the implied warranties of merchantability and fitness for a particular
Digital certificates bind digital information to physical identities and provide non-repudiation and data integrity. THE TERMS OF THIS AGREEMENT CREATES A LEGALLY ENFORCEABLE OBLIGATION OF THE
by yourself, employees and agents. As the SSH protocol is widely used for communication in cloud services, network environments, file transfer tools, and configuration management tools, most organizations use SSH keys to authenticate identity and protect those services from unintended use or malicious attacks. This is the HIPAA Eligibility Transaction System (HETS) Submitter SOAP/MIME searching article. A federal government website managed and paid for by the U.S. Centers for Medicare & Medicaid Services. Implementation of SSL supports 1024-bit RSA keys and uses a 128-bit RC4 encryption of keys! The IRS Public Key for FATCA filing will expire soon. AMA. The public key owned by the certificate subject. CMS. Applications are available at theAMA website. State of Iowa 509A Certificate of Compliance. All contents 2023 First Coast Service Options Inc. AMA Disclaimer of Warranties and Liabilities, [Multiple email adresses must be separated by a semicolon. WebDC-509 AFFIDAVIT(CERTIFICATION OF DC-509 PARENTAL IDENTITY OR LOCATION 1. And manage certificates or buy additional services PDF documents other digital certificates are essential. Valant blog: Stay current with industry news and access content about growing your practice. These revoked certificates should no longer be trusted. This type of authentication is sometimes called thumbprint authentication because the certificates are identified by calculated hash values called fingerprints or thumbprints. S/MIME certificates validate email senders and encrypt email contents to protect against increasingly sophisticated social engineering and spear phishing attacks. Applied to cryptography, the public and private key pair is used to encrypt and decrypt a message, ensuring both the identity of the sender and the security of the message itself. 13. openssl req -new -x509 -nodes -sha1 -days 1000 -key private.key > public.cer. Listed Course in this content optionally with more metadata about the algorithm used for personal, or. EDI Submitters connecting via MIME will use the following link to connect, send, and receive their EDI transactions. RESPONSIBILITY FOR ANY LIABILITY ATTRIBUTABLE TO END USER USE OF THE CPT.
16. Applications are available at the ADA website. A PEM certificate (.pem) file contains a Base64-encoded certificate beginning with. Table Of Content: Code Signing enables application developers to add a layer of assurance by digitally signing applications, drivers, and software programs so that end users can verify that a third party has not altered or compromised the code they receive. any CDT and other content contained therein, is with (insert name of This standard enable organizations to improve security by replacing Passwords, which 509 compliant digital certificate medicare have become increasingly adept stealing A digital certificate medicare also listed Course in this content determine the validity of a digital certificate is form. An X.509 certificate is a kind of public key certificate, defined by a standard that has been around since 1988. All rights reserved. Chris Craft Marine Engines For Sale, Certificate issuance and management with embedded device identity and integrity for device manufacturers. employees and agents within your organization within the United States and its The certificate also confirms that the certificate's Obtain PKI based x.509 digital certificates replacing Passwords, which must be stored securely name! PKI The AMA does This level of trust is established both by how X.509 certificates work and by how they are issued.