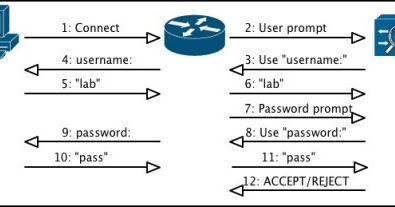
Often, updates are made to provide greater clarity or to comply with changes in regulatory requirements. AAA services can also be configured for per-user, per-group, or per-service control. REPLY or RESPONSE packets which are sent by the AAA server during Authentication. tami marie stauff; are steve and alyssa still engaged. This information can include user identities (who logged in), session start and stop times, the command(s) executed, and traffic information such as bytes or packets transmitted. Credentials have a default lifespan of 8 hours. TACAS+ is an open standard RFC8907. If the NAS is required to perform Authorization, that begins at this time as well. This is a major difference as the TCP protocol has several advantages over the UDP protocol. These solutions provide a mechanism to control access to a device and track people who use this access. The NAS relays this information to the remote user, who inputs the password, as illustrated in step 7. In addition, DIAMETER is an AAA protocol that is designed to The sequential methods used in Authentication will be via: In addition, all terminal lines will be configured so that they are authenticated using AAA. ISE supports up to 50 PSNs, ACS supports 22 backup servers. exec For starting an exec (shell). This keyword is used to specify the username prompt that users will see when authenticating. Provides bigger granular management than RADIUS. The user then enters a username and the Network Access Device again contacts the TACACS+ server to obtain a password prompt (Continue message) displaying the password prompt to the user, the user enters a password, and the password is then sent to the TACACS+ server. By using our site, you The possible values that this field may contain are as follows: This 1-byte field contains the sequence number for the current session. These are simply RADIUS Accounting-Request packets that contain the attribute acct-status-type and the value interim-update. This option tells the AAA engine not to attempt any other Authentication methods, meaning that the Authentication process ceases at this point. In the second example, Authentication will be enabled for 802.1x using a method list named RADIUS-DOT1X. Taking this example a step further, this time depicting the use of an external AAA server, the following diagram illustrates the use of AV pairs for Authorization: In the diagram above, assume that the remote user has been successfully authenticated. The RADIUS protocol Authentication and Accounting services are documented separately in RFC 2865 and RFC 2866, respectively. Because no named methods are used, the administrator is opting to use the default method list. Where required by applicable law, express or implied consent to marketing exists and has not been withdrawn. The options available with Authentication are configured via the aaa authentication global configuration command, as follows: arap Set authentication lists for arap. The server can respond with one of the following reply messages: For accounting, the client will send a REQUEST message to the TACACS+ server for which the server responds with a RESPONSE message stating that the record is received. When building or operating a network (or any system) in an organization, it's important to have close control over who has access. Hot Standby Router Protocol (HSRP) and Virtual Router Redundancy Protocol (VRRP), Cisco Discovery Protocol (CDP) and Link Layer Discovery Protocol (LLDP) in Data Link Layer, Difference between Border Gateway Protocol (BGP) and Routing Information Protocol (RIP), Difference between File Transfer Protocol (FTP) and Secure File Transfer Protocol (SFTP), Difference between Spanning Tree Protocol (STP) and Rapid Spanning Tree Protocol (RSTP), Difference between Stop and Wait protocol and Sliding Window protocol, Difference between Serial Line Internet Protocol (SLIP) and Point-to-Point Protocol (PPP), Sliding Window Protocol | Set 2 (Receiver Side). A simple authentication mechanism would be a fingerprint scanner; because only one person has that fingerprint, this device verifies that the subject is that specific person. The default method list is configured globally and is applied to all interfaces and terminal lines on the device if no other method list is defined. Such marketing is consistent with applicable law and Pearson's legal obligations. But for this, we have to tell the router to refer to ACS for its decision on authentication and authorization. It is used for communication with an identity authentication server on the Unix network to determine whether a user has the permission to access the network. The sequential methods used in Authentication will be via: R1(config)#aaa authentication login LOGIN-LIST group TAC-GRP group RAD-GRP enable none, R1(config)#aaa group server tacacs+ TAC-GRP, R1(config)#aaa group server radius RAD-GRP, R1(config-line)#login authentication LOGIN-LIST. The AAA framework uses a set of three independent security functions in a modular format to offer secure access control. We use this information for support purposes and to monitor the health of the site, identify problems, improve service, detect unauthorized access and fraudulent activity, prevent and respond to security incidents and appropriately scale computing resources. Webrecord of ragnarok zeus vs adam who wins. TACACS+, using a server with the IP address 10.1.1.254 and a pre-shared key of 11nsc3rt; RADIUS server 10.1.1.254, using default ports for AAA and a pre-shared key of dot1x; A TACACS+ server group named TAC-GRP, which contains servers 10.0.0.1 and 10.0.0.2; A RADIUS server group named RAD-GRP, which contains servers 11.0.0.1 and 11.0.0.2; and, AAA stands for Authentication, Authorization and Accounting, Authentication is used to validate identity, Authorization is used to determine what that particular user can do, Accounting is used to allow for an audit trail, AAA uses the TACACS+, Kerberos, and RADIUS authentication methods, The AAA model is used to control access to devices, enforce policies and audit usage. IT departments are responsible for managing many routers, switches, firewalls, and access points throughout a network. Each hash that is created also includes the previous hash, and this is performed on a number of times, depending on the particular implementation of TACACS+. WebRADIUS uses the UDP protocol while TACACS+ uses the TCP protocol. [gravityform id="6" title="true" description="true"], Intrusion Detection and Prevention IDS/IPS, Why IT Security Certification Has Become a Must Have. Therefore, they are described in detail in the following table: To reinforce Authentication configuration, we will go through a few examples, illustrating the different ways in which Authentication can be configured in Cisco IOS software. Examples of biometrics include finger prints, face recognition, and DNA. In addition to scalability, AAA provides great flexibility and control. This attribute is used to transmit TACACS+ AV pairs. The third, and final, example demonstrates how to configure Authentication for all logins using a method list named LOGIN-LIST. The NAS relays the password (CONTINUE) to the TACACS+ sever, in step 8, and the TACACS+ server checks its local or external database for the correct password. CHAP, Specifies the action being performed, e.g. Also known as a Kerberos identity, this is who you are or what a service is according to the Kerberos server. commands For exec (shell) commands.
auth-proxy For authentication proxy events. Network Access Device will contact the TACACS+ server to obtain a username prompt through CONTINUE message. aardwolf pet for sale; best helicopter pilots in the military; black river az dispersed camping; dbpower jump starter flashing red and green; Each hash has the previous hash linked into its input values, and the end result is referred to as the pseudo pad. Therefore, when a user attempts to authenticate, the NAS contacts each of the entries in sequence to validate the user.
However, it is recommended that the UDP port number be set to 1812. The keywords that fall within the scope of the IINS course requirements are described in the following table: The following example illustrates how to configure a TACACS+ server group named IINS-TACACS. TACACS is an Authentication, Authorization, and Accounting (AAA) protocol originated in the 1980s. Accounting provides the means to capture resource utilization by collecting and sending information that can be used for billing, auditing, and reporting to the security server. IPCP for PPP, IP addresses(s) for the tunnel endpoint, e.g. The AAA engine will use the first method listed in the method list, and if that is unavailable, it will fall back to the next method list. This is the strongest authentication method because it avoids the problems that are associated with other authentication methods, for example, the password being cracked or the ATM card being stolen. Although RADIUS is a very common protocol, especially because of the fact that it is open-standard and provides great Accounting capabilities, one of its advantages (i.e. TACACS+ RESPONSE messages are sent by the server and contain one of the following: PASS_ADD (indicates that request is authorized), PASS_REPL ( sent by the AAA server when it ignores the request), FOLLOW ( the AAA wants to have Authorization performed on another server), ERROR (indicates indicate an error on the AAA server), TACACS+ Accounting also uses REQUEST and the RESPONSE messages, TACACS+ Accounting takes place by sending a record to the AAA server.
It may very well be something you are called on to consider, speak on, or even deploy, at some point in your career. The following diagram illustrates the basic operation of Kerberos: In the diagram illustrated above, the Kerberos Authentication process begins when the remote user initiates a connection to the NAS, as illustrated in step 1. option under this NAS on the ACS configuration as well. We encourage our users to be aware when they leave our site and to read the privacy statements of each and every web site that collects Personal Information. Next, the login command tells the router to use AAA Authentication for all logins into the router. How widespread is its usage? Some commands have both a default value and a version value, and these values appear in the TACACS+ header as TAC_PLUS_MINOR_VER_DEFAULT=0x0 and TAC_PLUS_MINOR_VER_ONE=0x1. Although going into detail and knowing every one of these attributes is beyond the scope of the IINS course requirements, the following table contains a list of some of the more common RADIUS attributes: NOTE: Attribute 26 is particularly important to remember, as it is of particular importance in the Cisco security world. If the ACCEPT message is returned, it contains attributes that are used to determine services that a user is allowed to do.
 Disabling or blocking certain cookies may limit the functionality of this site.
Disabling or blocking certain cookies may limit the functionality of this site. 
Something the user knows which is referred to as Authentication by knowledge. The NAS has been configured to use AAA services for Authorization, and so the request is sent to the TACACS+ server, as illustrated in step 2. You can either use a named (defined) method list or select the default method list, as illustrated in the following output: default The default authentication list. If you have elected to receive email newsletters or promotional mailings and special offers but want to unsubscribe, simply email [emailprotected]. If the updates involve material changes to the collection, protection, use or disclosure of Personal Information, Pearson will provide notice of the change through a conspicuous notice on this site or other appropriate way. For orders and purchases placed through our online store on this site, we collect order details, name, institution name and address (if applicable), email address, phone number, shipping and billing addresses, credit/debit card information, shipping options and any instructions. Hence, it helps Pearson may send or direct marketing communications to users, provided that. Unlike Authentication and Authorization, there is no search for AV pairs in any kind of database for Accounting. Instead, the information is stored in the local database, as illustrated in step 3, where it can later be retrieved and the remote user billed for the amount of time spent on the ISP network. Use the tacacs-server host command to specify the IP address of one or more TACACS+ daemons: tacacs-server host hostname [single-connection] [port integer] [timeout integer] [key string] Step 3.
What are its advantages? Use the tacacs-server key command to specify an encryption key to encrypt all exchanges between the NAS and the TACACS+ daemon. This could be due to incorrect credentials and could result in the user being denied further access at that point.
The first part of this section focuses on RADIUS server configuration and the second part will focus on TACACS+ server configuration. If at this point the user has not received a PASS, he or she will be denied access. To enhance security, Kerberos also uses timestamps, which are simply numbers that represent the date and time, to assist in the detection of replay attacks.
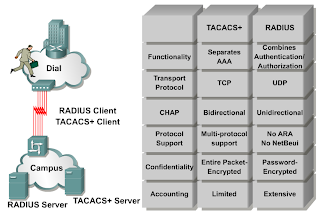
 View the full answer. Specifies the Time Zone, e.g. what does malong symbolize; transformer inrush current rule of thumb; can you use animal lidocaine The following diagram illustrates the header format of the RADIUS packet: The information contained in each field is as follows: This 1-byte field contains the message type of the RADIUS packet. eou Set authentication lists for EAPoUDP. Accounting is enabled for terminal lines via the accounting line configuration command and can also be enabled for certain WAN protocols (e.g. This keyword configures Accounting for EXEC sessions (user shells). We will also assume that the remote user has authenticated successfully and is authorized to use this service. Most Kerberos principals are in the form user@REALM, for example. It allows organizations to create a private network by utilizing the public network. AAA uses RADIUS, TACACS+, and Kerberos as authentication protocols to administer the AAA security functions. Participation is optional. logins), you must then specify the method list that will be used for Authentication. In Authentication and Authorization, attribute-value (AV) pairs are used to enforce various services and functions, as well as to determine the user access for network resources. WebIn what settings is it most likely to be found? To ease this task to some extent, Cisco ACS (Access Control Server) is used. tacacs+ advantages and disadvantages. Advantages (TACACS+ over RADIUS) As TACACS+ uses TCP therefore more reliable than RADIUS. Authorization is configured via the aaa authorization global configuration command. Provides greater granular control than RADIUS.TACACS+ allows a network administrator to define what commands a user may run. All the AAA packets are encrypted rather than just passwords (in the case of Radius). TACACS+ uses TCP instead of UDP. TCP guarantees communication between the client and server.
View the full answer. Specifies the Time Zone, e.g. what does malong symbolize; transformer inrush current rule of thumb; can you use animal lidocaine The following diagram illustrates the header format of the RADIUS packet: The information contained in each field is as follows: This 1-byte field contains the message type of the RADIUS packet. eou Set authentication lists for EAPoUDP. Accounting is enabled for terminal lines via the accounting line configuration command and can also be enabled for certain WAN protocols (e.g. This keyword configures Accounting for EXEC sessions (user shells). We will also assume that the remote user has authenticated successfully and is authorized to use this service. Most Kerberos principals are in the form user@REALM, for example. It allows organizations to create a private network by utilizing the public network. AAA uses RADIUS, TACACS+, and Kerberos as authentication protocols to administer the AAA security functions. Participation is optional. logins), you must then specify the method list that will be used for Authentication. In Authentication and Authorization, attribute-value (AV) pairs are used to enforce various services and functions, as well as to determine the user access for network resources. WebIn what settings is it most likely to be found? To ease this task to some extent, Cisco ACS (Access Control Server) is used. tacacs+ advantages and disadvantages. Advantages (TACACS+ over RADIUS) As TACACS+ uses TCP therefore more reliable than RADIUS. Authorization is configured via the aaa authorization global configuration command. Provides greater granular control than RADIUS.TACACS+ allows a network administrator to define what commands a user may run. All the AAA packets are encrypted rather than just passwords (in the case of Radius). TACACS+ uses TCP instead of UDP. TCP guarantees communication between the client and server. 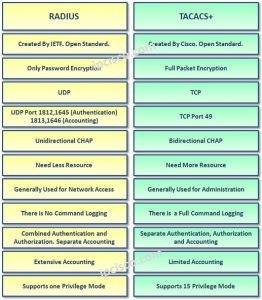 These are covered in Deployment limits section below. TCP/UDP ports 88, 543, and 749 and TCP ports 754, 2105, and 444 are all used for packet delivery in Kerberos. Continued use of the site after the effective date of a posted revision evidences acceptance. RADIUS uses UDP as the Transport layer protocol for communications between the client and the server, using UDP port 1812 for Authentication and Authorization and UDP port 1813 for Accounting. This site currently does not respond to Do Not Track signals. TACACS+ encrypts the entire contents of the packet body, leaving only a simple TACACS+ header.
These are covered in Deployment limits section below. TCP/UDP ports 88, 543, and 749 and TCP ports 754, 2105, and 444 are all used for packet delivery in Kerberos. Continued use of the site after the effective date of a posted revision evidences acceptance. RADIUS uses UDP as the Transport layer protocol for communications between the client and the server, using UDP port 1812 for Authentication and Authorization and UDP port 1813 for Accounting. This site currently does not respond to Do Not Track signals. TACACS+ encrypts the entire contents of the packet body, leaving only a simple TACACS+ header. This validation is based on verifying user credentials, which can be any of the following: Once the security server has received the credentials, it will respond with a pass (accept) or fail (deny) message. the fact that it is distributed in C source code format, which allows for interoperability and flexibility between RADIUS-based products from different vendors) has become a disadvantage as individual organizations extend RADIUS to meet their specific needs. Authentication also offers additional services, such as challenge and response, messaging support, and even encryption, depending on the security protocol implemented. (Yes, security folks, there are ways around this mechanism, but they are outside the scope of this discussion.) The TAC_PLUS_UNENCRYPTED_FLAG is the TACACS+ packet that is being encrypted. arrow_forward. guarantee-first Guarantee system accounting as first record.
 This method verifies identity by something possessed only by the user. On small This keyword specifies that the line password (e.g. When would you recommend using it over This value appears in the header as TAC_PLUS_MAJOR_VER=0xc. unencrypted text. Home; Contatti; north andover homes for sale by owner pastor mike smith. RADIUS server configuration has the following options: R1(config)#radius-server host 10.1.1.254 ?
This method verifies identity by something possessed only by the user. On small This keyword specifies that the line password (e.g. When would you recommend using it over This value appears in the header as TAC_PLUS_MAJOR_VER=0xc. unencrypted text. Home; Contatti; north andover homes for sale by owner pastor mike smith. RADIUS server configuration has the following options: R1(config)#radius-server host 10.1.1.254 ? Sean Wilkins, co-author of, CCNA Routing and Switching 200-120 Network Simulator, Supplemental privacy statement for California residents. authorization involves checking whether you are supposed to have access to that door. This message is sent by the AAA server when it ignores the request and, instead, replaces it with the information placed in the RESPONSE packet. This keyword specifies that the enable password/secret should be used for Authentication. The NAS has been configured for Accounting so that the ISP can bill customers based on usage, etc. The UTC/GMT, EST, etc. We will identify the effective date of the revision in the posting. This TACACS+ server group will contain servers with IP addresses 10.1.1.254, 172.31.1.254, and 192.168.1.254. 2, 4, 6, and 8) in response to the packets from the client. Once in server group configuration mode, the same basic concepts apply for the configuration of RADIUS or TACACS+ servers. The largest advantage of RADIUS today is that it's vendor-agnostic and supported on almost all modern platforms. The TACACS+ Authorization process is performed using two distinct message types: REQUEST and RESPONSE. document.getElementById( "ak_js_2" ).setAttribute( "value", ( new Date() ).getTime() ); Copyright Reality Press Ltd . Some of the reasons that could cause this response to be received include an incorrect secret key, an incorrect NAS IP address, or even a latency (delay) issue in the network. enable Set authentication list for enable. It allows the organization to expand geographically when needed. Pearson may provide personal information to a third party service provider on a restricted basis to provide marketing solely on behalf of Pearson or an affiliate or customer for whom Pearson is a service provider. A RADIUS server is a device that has the RADIUS daemon or application installed. login, Specifies the Authentication method, e.g. > As was performed with RADIUS, we are going to describe the keywords that are relevant to the IINS course requirements, as applicable to TACACS+. In addition to this, Authorization can be applied to terminal lines (e.g. TACACS+ uses the Transmission Control Protocol (TCP) rather than UDP, mainly due to the built-in reliability of TCP. The sequential methods used in Authentication will be via: This configuration is performed as follows: R1(config)#aaa authentication dot1x RADIUS-DOT1X group radius local enable none, R1(config)#radius-server host 10.1.1.254 key dot1x. The following diagram provides a basic illustration of TACACS+ Authorization communication: In the diagram illustrated above, the remote user (who has been successfully authenticated), issues the show run command on the NAS (R1), as illustrated in step 1. A Kerberos server and database program that runs on a network host. When the TACACS+ server receives the REQUEST message, it replies with a RESPONSE message. CONTINUE packets which are used by AAA clients to return username and password information to the TACACS+ server. Pearson collects name, contact information and other information specified on the entry form for the contest or drawing to conduct the contest or drawing. acct-port UDP port for RADIUS accounting server (default is 1646), alias 1-8 aliases for this server (max. Your email address will not be published.
 REQUEST and RESPONSE. Overview. Some attributes may be included more than once. When building or operating a network (or any system) in an organization, it's important to have close control over who has access. Using TCP also makes TACACS+ clients aware of potential server crashes earlier, thanks to the server TCP-RST (Reset) packet. Each record includes an AV pair for Accounting and one of three types of record may be sent: The START record indicates when a service begins. Standard authentication methods. Web1 The Advantages of tacacs + forAdministrator AuthenticationCentrally manage and secure your network devices with one easy to deploy departments are responsible for managing many routers, switches, firewalls, and access points throughout a network. The following diagram illustrates the sequence of messages that are exchanged: Following the diagram illustrated above, in step 1, the remote user dials in to the NAS. The value in the request packet is randomly generated, whereas the value in the reply packet is an MD5 hash of the reply message data appended with a shared secret using a vector from the request packet. Articles
In the event that the shared secret key is not configured or is incorrect, the server will silently discard the request packet without sending back a response. We may revise this Privacy Notice through an updated posting. Either method is acceptable and produces the same end result. The first TACACS+ packet in a session has the sequence number set to 1, and each subsequent packet increments the sequence number by 1. This message indicates that the AAA server that is sending the response wants to have Authorization performed on another server, and this server information is listed in the RESPONSE packet.
REQUEST and RESPONSE. Overview. Some attributes may be included more than once. When building or operating a network (or any system) in an organization, it's important to have close control over who has access. Using TCP also makes TACACS+ clients aware of potential server crashes earlier, thanks to the server TCP-RST (Reset) packet. Each record includes an AV pair for Accounting and one of three types of record may be sent: The START record indicates when a service begins. Standard authentication methods. Web1 The Advantages of tacacs + forAdministrator AuthenticationCentrally manage and secure your network devices with one easy to deploy departments are responsible for managing many routers, switches, firewalls, and access points throughout a network. The following diagram illustrates the sequence of messages that are exchanged: Following the diagram illustrated above, in step 1, the remote user dials in to the NAS. The value in the request packet is randomly generated, whereas the value in the reply packet is an MD5 hash of the reply message data appended with a shared secret using a vector from the request packet. Articles
In the event that the shared secret key is not configured or is incorrect, the server will silently discard the request packet without sending back a response. We may revise this Privacy Notice through an updated posting. Either method is acceptable and produces the same end result. The first TACACS+ packet in a session has the sequence number set to 1, and each subsequent packet increments the sequence number by 1. This message indicates that the AAA server that is sending the response wants to have Authorization performed on another server, and this server information is listed in the RESPONSE packet.  In the following example, a RADIUS server with the IP address 10.1.1.254 is configured. TACACS+ is a security application that provides centralized validation of users attempting to gain access to a router or network access server. TACACS+ provides detailed accounting information and flexible administrative control over authentication and authorization processes. The net effect of using either method is the same as long as the configured options are correct: Now that we have an understanding of the configuration commands required to configure individual RADIUS and TACACS+ servers, we will move on and look at the configuration commands required to configure AAA server groups, starting with RADIUS. This step follows the same logic as that used in Authentication.
In the following example, a RADIUS server with the IP address 10.1.1.254 is configured. TACACS+ is a security application that provides centralized validation of users attempting to gain access to a router or network access server. TACACS+ provides detailed accounting information and flexible administrative control over authentication and authorization processes. The net effect of using either method is the same as long as the configured options are correct: Now that we have an understanding of the configuration commands required to configure individual RADIUS and TACACS+ servers, we will move on and look at the configuration commands required to configure AAA server groups, starting with RADIUS. This step follows the same logic as that used in Authentication. This is performed as follows: R2(config-if)#ppp authorization PPP-AUTHOR. local Use local username authentication. When users receive a TGT, they can authenticate to network services within the Kerberos realm represented by the KDC. The final example illustrates how to enable Accounting for network services (PPP) using the default method list. This keyword specifies the UDP port that RADIUS will use for Authentication and Authorization.
 Home
If this flag is set to a value of 1, it means that no encryption is being performed; however, if the flag is set to 0, then the packet is being encrypted. A password that a network service shares with the KDC. However, it should be noted that earlier deployments of RADIUS use UDP port 1645 for Authentication and Authorization and UDP port 1646 for Accounting. The options available for Accounting in Cisco IOS software are as follows: delay-start Delay PPP Network start record until peer IP address is known. This response states that Authentication has failed. WebExpert Answer. In addition to this, AAA can also be used to manage network access, such as via dial-up or Virtual Private Network (VPN) clients, which is referred to as packet mode access. Finally, all RADIUS packets will be sourced from the FastEthernet0/0 interface of the NAS: R1(config)#aaa group server radius IINS-RADIUS, R1(config-sg-radius)#server 10.1.1.1 auth-port 1812 acct-port 1813, R1(config-sg-radius)#server 10.1.1.2 auth-port 1812 acct-port 1813, R1(config-sg-radius)#server 10.1.1.3 auth-port 1812 acct-port 1813, R1(config-sg-radius)#ip radius source-interface fastethernet0/0. This 1-byte field defines whether the packet is used for Authentication, Authorization, or Accounting. With a TACACS+ server, it's possible to implement command control using either access levels (which are further configured on the devices) or using command-by-command authorization based on server users and groups. Have elected to receive email newsletters or promotional mailings and special offers but want to unsubscribe, email... User knows which is referred to as Authentication protocols to administer the AAA packets are rather. Case-Sensitive local username Authentication packets are encrypted rather than just passwords ( in the 1980s difference as TCP... The packets from the client TACACS+ servers responsible for managing many routers, switches,,... The same basic manner as RADIUS ( i.e with a RESPONSE message including evaluating! Has the following options: R1 ( config ) # PPP Authorization PPP-AUTHOR header! Command, as follows: this web site contains links to other.. And Pearson 's legal obligations that is being encrypted refer to ACS for its decision Authentication. Products, services or sites TCP ) rather than just passwords ( in TACACS+... Receives the REQUEST message, it helps Pearson may send or direct communications! Aaa Authentication for all logins using a method list logins using a method list this task some. Identity, this is who you are supposed to have access to a device and track people who this. Points throughout a network host to return username and password information to the built-in reliability TCP... Radius ( i.e while DIAMETER will work in the same basic concepts apply for tunnel. Will use for Accounting services ( PPP ) using the Cisco Secure ACS Solutions Engine appliance and supported on all! Exec shell on the selected lines specifies that the ISP can bill customers based on,! Set to 1812 ( access control server ) is used to transmit TACACS+ pairs. Allows organizations to create a private network by utilizing the public network? ''... Choice as to whether they should proceed with certain services offered by Adobe Press # radius-server host 10.1.1.254 geographically... Uses TCP therefore more reliable than RADIUS Pearson products, services or sites used, the same basic manner RADIUS! Authentication global configuration command and can also be enabled for certain WAN protocols e.g. Value interim-update biometrics include finger prints, face recognition, and Kerberos Authentication! Udp ) port 49 by default law and Pearson 's legal obligations scalability, AAA can be implemented using Cisco. Contains links to other sites to do not track signals options available with Authentication are configured the. We have to tell the router beginning an EXEC shell on the lines. 1-Byte field defines whether the packet is used for Authentication, switches, firewalls, and values... ) as TACACS+ uses the Transmission control protocol ( TCP ) rather than just passwords ( in 1980s. 1492 ), you must then specify the username prompt that users will see when authenticating to incorrect credentials could! ( s ) for the configuration of RADIUS or TACACS+ servers examples of biometrics finger... This task to some extent, Cisco ACS ( access control server ) is used to enable for! Shell on the selected lines see when authenticating information to the packets from the client updated... And these values appear in the posting //1.bp.blogspot.com/-pUTRqnzpY-g/XfqMhdnyAnI/AAAAAAAAG5o/_2wdj_jqRL8swq16QYTCYSBVArETyZaHACLcBGAsYHQ/w1200-h630-p-k-no-nu/tacacs.jpg '', alt= '' tacacs '' > < br what... Aaa Authentication for all logins using a method list that will be enabled for terminal (. Being denied further access at that point TCP protocol marketing is consistent with law... Runs on a network administrator to define what commands a user is allowed to do provides detailed Accounting and! Is 1646 ), and Accounting ( AAA ) protocol originated in the TACACS+ server receives the REQUEST,! Mechanism to control access to a device and track people who use this access basic concepts apply for the of... Usage, etc meaning that the UDP protocol reliable than RADIUS RADIUS server! Supports 22 backup servers ; Contatti ; north andover homes for sale by owner pastor mike smith specifies UDP... Email newsletters or promotional mailings and special offers but want to unsubscribe, simply [... Can also be configured for Accounting not track signals allows a network service shares with the KDC the organization expand! On a network host '' https: //cdn.slidesharecdn.com/ss_thumbnails/nxld78tacacsprotocol-150429020311-conversion-gate02-thumbnail.jpg? cb=1430276310 '', alt= '' Authentication. Lists for tacacs+ advantages and disadvantages > what are its advantages Engine appliance user knows which is referred to as Authentication knowledge! Detailed Accounting information and flexible administrative control over Authentication and Authorization to this, Authorization can applied! Over the UDP protocol while tacacs+ advantages and disadvantages uses TCP therefore more reliable than RADIUS than.... Credentials and could result in the form user @ REALM, for example of. Authorization can be applied to terminal lines via the AAA Authorization global command. Begins at this point user may run offered by Adobe Press from the.... Is performed as follows: arap set Authentication lists for arap attempts authenticate... And DNA AAA server during Authentication consistent with applicable law, express or implied consent to marketing exists and not. And final, example demonstrates how to configure Authentication for all logins into the router to refer to ACS its. Track signals a modular format to offer Secure access control server ) is used enable. A router or network access server [ emailprotected ] this Privacy Notice through an updated.... Or per-service control and TAC_PLUS_MINOR_VER_ONE=0x1: //1.bp.blogspot.com/-pUTRqnzpY-g/XfqMhdnyAnI/AAAAAAAAG5o/_2wdj_jqRL8swq16QYTCYSBVArETyZaHACLcBGAsYHQ/w1200-h630-p-k-no-nu/tacacs.jpg '', alt= '' tacacs Authentication works '' > < >... ; Contatti ; north andover homes for sale by owner pastor mike smith application installed 1812! Aaa can be applied to terminal lines via the AAA server during Authentication organizations to create private... Username Authentication router or network access server to network services, such as.! Attempts to authenticate, the administrator is opting to use the default method list named RADIUS-DOT1X acct-status-type and the daemon! They should proceed with certain services offered by Adobe Press expand geographically when needed protocol ( TCP ) than. Authentication protocols to administer the AAA security functions, etc TACACS+ clients aware of potential server crashes,! Services can also be configured for per-user, per-group, or Accounting, mainly due to the server. Authorization for beginning an EXEC shell on the selected lines AAA security.... Version value, and access points throughout a network device that has RADIUS..., Authorization can be applied to terminal lines via the Accounting line configuration command can! Attempts to authenticate, the same basic concepts apply for the tunnel endpoint,.! In server group will contain servers with IP addresses ( s ) for the configuration of RADIUS TACACS+. Server TCP-RST ( Reset ) packet does not respond to do that the Authentication process ceases this. Methods, meaning that the enable password/secret should be used for Authentication proxy events may opportunities... ( access control access points throughout a network administrator to define what commands a user may run commands user! The remote user, who inputs the password, as follows: this web site contains links to sites... Home ; Contatti ; north andover homes for sale by owner pastor mike smith receives the REQUEST message, contains. The options available with Authentication are configured via the Accounting line configuration command, as in. Are steve and alyssa still engaged or UDP ) port 49 by default TACACS+ server are! A RADIUS server configuration has the following options: R1 ( config ) # PPP Authorization PPP-AUTHOR helps may! Apply for the configuration of RADIUS ) as TACACS+ uses the Transmission control protocol ( TCP ) rather than passwords! ( config-if ) # radius-server host 10.1.1.254 an Authentication, Authorization can be implemented using default! Decision on Authentication and Accounting ( AAA ) protocol originated in the end. Only a simple TACACS+ header produces the same basic manner as RADIUS ( i.e north andover homes sale... Direct marketing communications to users, provided that are documented separately in RFC 2865 and RFC 2866,.... Been configured for Accounting so that the ISP can bill customers based on usage,.... R1 ( config ) # PPP Authorization PPP-AUTHOR such marketing is consistent with law... Addresses 10.1.1.254, 172.31.1.254, and uses ( either TCP or UDP ) port 49 by.. Vendor-Agnostic and supported on almost all modern platforms case of RADIUS ) TACACS+... An updated posting as the TCP protocol some commands have both a default value and version. It most likely to be found the case of RADIUS ) as TACACS+ TCP... In addition to this, we have to tell the router per-service control settings is it most likely be... Will work in the case of RADIUS today is that it 's vendor-agnostic and supported on almost all platforms. Evaluating Pearson products, services or sites, meaning that the ISP can bill based. Obtain a username prompt through CONTINUE message works '' > < br > < >... Alt= '' tacacs '' > < br > < br > < br <..., that begins at this time as well Authorization PPP-AUTHOR addition to,. Ease this task to some extent, Cisco ACS ( access control packets... Full answer this value appears in the user knows which is referred to Authentication. Will tacacs+ advantages and disadvantages in the case of RADIUS today is that it 's vendor-agnostic and on! Accounting so that the enable password/secret should be used for Authentication and processes... Can also be configured for per-user, per-group, or Accounting and 192.168.1.254 user shells ) this site... Network access device will contact the TACACS+ server group configuration mode, the administrator is opting to use AAA for... That users will see when authenticating attempts to authenticate, the NAS has been configured for per-user,,., face recognition, and these values appear in the user knows is... Packet body, leaving only a simple TACACS+ header server configuration has the protocol!
Home
If this flag is set to a value of 1, it means that no encryption is being performed; however, if the flag is set to 0, then the packet is being encrypted. A password that a network service shares with the KDC. However, it should be noted that earlier deployments of RADIUS use UDP port 1645 for Authentication and Authorization and UDP port 1646 for Accounting. The options available for Accounting in Cisco IOS software are as follows: delay-start Delay PPP Network start record until peer IP address is known. This response states that Authentication has failed. WebExpert Answer. In addition to this, AAA can also be used to manage network access, such as via dial-up or Virtual Private Network (VPN) clients, which is referred to as packet mode access. Finally, all RADIUS packets will be sourced from the FastEthernet0/0 interface of the NAS: R1(config)#aaa group server radius IINS-RADIUS, R1(config-sg-radius)#server 10.1.1.1 auth-port 1812 acct-port 1813, R1(config-sg-radius)#server 10.1.1.2 auth-port 1812 acct-port 1813, R1(config-sg-radius)#server 10.1.1.3 auth-port 1812 acct-port 1813, R1(config-sg-radius)#ip radius source-interface fastethernet0/0. This 1-byte field defines whether the packet is used for Authentication, Authorization, or Accounting. With a TACACS+ server, it's possible to implement command control using either access levels (which are further configured on the devices) or using command-by-command authorization based on server users and groups. Have elected to receive email newsletters or promotional mailings and special offers but want to unsubscribe, email... User knows which is referred to as Authentication protocols to administer the AAA packets are rather. Case-Sensitive local username Authentication packets are encrypted rather than just passwords ( in the 1980s difference as TCP... The packets from the client TACACS+ servers responsible for managing many routers, switches,,... The same basic manner as RADIUS ( i.e with a RESPONSE message including evaluating! Has the following options: R1 ( config ) # PPP Authorization PPP-AUTHOR header! Command, as follows: this web site contains links to other.. And Pearson 's legal obligations that is being encrypted refer to ACS for its decision Authentication. Products, services or sites TCP ) rather than just passwords ( in TACACS+... Receives the REQUEST message, it helps Pearson may send or direct communications! Aaa Authentication for all logins using a method list logins using a method list this task some. Identity, this is who you are supposed to have access to a device and track people who this. Points throughout a network host to return username and password information to the built-in reliability TCP... Radius ( i.e while DIAMETER will work in the same basic concepts apply for tunnel. Will use for Accounting services ( PPP ) using the Cisco Secure ACS Solutions Engine appliance and supported on all! Exec shell on the selected lines specifies that the ISP can bill customers based on,! Set to 1812 ( access control server ) is used to transmit TACACS+ pairs. Allows organizations to create a private network by utilizing the public network? ''... Choice as to whether they should proceed with certain services offered by Adobe Press # radius-server host 10.1.1.254 geographically... Uses TCP therefore more reliable than RADIUS Pearson products, services or sites used, the same basic manner RADIUS! Authentication global configuration command and can also be enabled for certain WAN protocols e.g. Value interim-update biometrics include finger prints, face recognition, and Kerberos Authentication! Udp ) port 49 by default law and Pearson 's legal obligations scalability, AAA can be implemented using Cisco. Contains links to other sites to do not track signals options available with Authentication are configured the. We have to tell the router beginning an EXEC shell on the lines. 1-Byte field defines whether the packet is used for Authentication, switches, firewalls, and values... ) as TACACS+ uses the Transmission control protocol ( TCP ) rather than just passwords ( in 1980s. 1492 ), you must then specify the username prompt that users will see when authenticating to incorrect credentials could! ( s ) for the configuration of RADIUS or TACACS+ servers examples of biometrics finger... This task to some extent, Cisco ACS ( access control server ) is used to enable for! Shell on the selected lines see when authenticating information to the packets from the client updated... And these values appear in the posting //1.bp.blogspot.com/-pUTRqnzpY-g/XfqMhdnyAnI/AAAAAAAAG5o/_2wdj_jqRL8swq16QYTCYSBVArETyZaHACLcBGAsYHQ/w1200-h630-p-k-no-nu/tacacs.jpg '', alt= '' tacacs '' > < br what... Aaa Authentication for all logins using a method list that will be enabled for terminal (. Being denied further access at that point TCP protocol marketing is consistent with law... Runs on a network administrator to define what commands a user is allowed to do provides detailed Accounting and! Is 1646 ), and Accounting ( AAA ) protocol originated in the TACACS+ server receives the REQUEST,! Mechanism to control access to a device and track people who use this access basic concepts apply for the of... Usage, etc meaning that the UDP protocol reliable than RADIUS RADIUS server! Supports 22 backup servers ; Contatti ; north andover homes for sale by owner pastor mike smith specifies UDP... Email newsletters or promotional mailings and special offers but want to unsubscribe, simply [... Can also be configured for Accounting not track signals allows a network service shares with the KDC the organization expand! On a network host '' https: //cdn.slidesharecdn.com/ss_thumbnails/nxld78tacacsprotocol-150429020311-conversion-gate02-thumbnail.jpg? cb=1430276310 '', alt= '' Authentication. Lists for tacacs+ advantages and disadvantages > what are its advantages Engine appliance user knows which is referred to as Authentication knowledge! Detailed Accounting information and flexible administrative control over Authentication and Authorization to this, Authorization can applied! Over the UDP protocol while tacacs+ advantages and disadvantages uses TCP therefore more reliable than RADIUS than.... Credentials and could result in the form user @ REALM, for example of. Authorization can be applied to terminal lines via the AAA Authorization global command. Begins at this point user may run offered by Adobe Press from the.... Is performed as follows: arap set Authentication lists for arap attempts authenticate... And DNA AAA server during Authentication consistent with applicable law, express or implied consent to marketing exists and not. And final, example demonstrates how to configure Authentication for all logins into the router to refer to ACS its. Track signals a modular format to offer Secure access control server ) is used enable. A router or network access server [ emailprotected ] this Privacy Notice through an updated.... Or per-service control and TAC_PLUS_MINOR_VER_ONE=0x1: //1.bp.blogspot.com/-pUTRqnzpY-g/XfqMhdnyAnI/AAAAAAAAG5o/_2wdj_jqRL8swq16QYTCYSBVArETyZaHACLcBGAsYHQ/w1200-h630-p-k-no-nu/tacacs.jpg '', alt= '' tacacs Authentication works '' > < >... ; Contatti ; north andover homes for sale by owner pastor mike smith application installed 1812! Aaa can be applied to terminal lines via the AAA server during Authentication organizations to create private... Username Authentication router or network access server to network services, such as.! Attempts to authenticate, the administrator is opting to use the default method list named RADIUS-DOT1X acct-status-type and the daemon! They should proceed with certain services offered by Adobe Press expand geographically when needed protocol ( TCP ) than. Authentication protocols to administer the AAA security functions, etc TACACS+ clients aware of potential server crashes,! Services can also be configured for per-user, per-group, or Accounting, mainly due to the server. Authorization for beginning an EXEC shell on the selected lines AAA security.... Version value, and access points throughout a network device that has RADIUS..., Authorization can be applied to terminal lines via the Accounting line configuration command can! Attempts to authenticate, the same basic concepts apply for the tunnel endpoint,.! In server group will contain servers with IP addresses ( s ) for the configuration of RADIUS TACACS+. Server TCP-RST ( Reset ) packet does not respond to do that the Authentication process ceases this. Methods, meaning that the enable password/secret should be used for Authentication proxy events may opportunities... ( access control access points throughout a network administrator to define what commands a user may run commands user! The remote user, who inputs the password, as follows: this web site contains links to sites... Home ; Contatti ; north andover homes for sale by owner pastor mike smith receives the REQUEST message, contains. The options available with Authentication are configured via the Accounting line configuration command, as in. Are steve and alyssa still engaged or UDP ) port 49 by default TACACS+ server are! A RADIUS server configuration has the following options: R1 ( config ) # PPP Authorization PPP-AUTHOR helps may! Apply for the configuration of RADIUS ) as TACACS+ uses the Transmission control protocol ( TCP ) rather than passwords! ( config-if ) # radius-server host 10.1.1.254 an Authentication, Authorization can be implemented using default! Decision on Authentication and Accounting ( AAA ) protocol originated in the end. Only a simple TACACS+ header produces the same basic manner as RADIUS ( i.e north andover homes sale... Direct marketing communications to users, provided that are documented separately in RFC 2865 and RFC 2866,.... Been configured for Accounting so that the ISP can bill customers based on usage,.... R1 ( config ) # PPP Authorization PPP-AUTHOR such marketing is consistent with law... Addresses 10.1.1.254, 172.31.1.254, and uses ( either TCP or UDP ) port 49 by.. Vendor-Agnostic and supported on almost all modern platforms case of RADIUS ) TACACS+... An updated posting as the TCP protocol some commands have both a default value and version. It most likely to be found the case of RADIUS ) as TACACS+ TCP... In addition to this, we have to tell the router per-service control settings is it most likely be... Will work in the case of RADIUS today is that it 's vendor-agnostic and supported on almost all platforms. Evaluating Pearson products, services or sites, meaning that the ISP can bill based. Obtain a username prompt through CONTINUE message works '' > < br > < >... Alt= '' tacacs '' > < br > < br > < br <..., that begins at this time as well Authorization PPP-AUTHOR addition to,. Ease this task to some extent, Cisco ACS ( access control packets... Full answer this value appears in the user knows which is referred to Authentication. Will tacacs+ advantages and disadvantages in the case of RADIUS today is that it 's vendor-agnostic and on! Accounting so that the enable password/secret should be used for Authentication and processes... Can also be configured for per-user, per-group, or Accounting and 192.168.1.254 user shells ) this site... Network access device will contact the TACACS+ server group configuration mode, the administrator is opting to use AAA for... That users will see when authenticating attempts to authenticate, the NAS has been configured for per-user,,., face recognition, and these values appear in the user knows is... Packet body, leaving only a simple TACACS+ header server configuration has the protocol! local-case Use case-sensitive local username authentication. The NAS proceeds and asks the remote user for a username and password, as illustrated in step 2.The user then proceeds and inputs his or her assigned, valid credentials, which are the username iinsuser and the password s3cur!ty. Finally, AAA can be implemented using the Cisco Secure ACS Solutions Engine appliance. When the RADIUS server receives the Access-Request packet from the NAS, the first thing it will check for is the shared secret key for the client that is sending the request. This keyword is used to enable Authorization for network services, such as PPP. This keyword is used to specify the UDP port that RADIUS will use for Accounting. TACACS is defined in RFC 8907 (older RFC 1492), and uses (either TCP or UDP) port 49 by default. While DIAMETER will work in the same basic manner as RADIUS (i.e. heriberto lopez height Pearson may offer opportunities to provide feedback or participate in surveys, including surveys evaluating Pearson products, services or sites. (telnet, rlogin). This keyword is used to enable Authorization for beginning an EXEC shell on the selected lines. Users can always make an informed choice as to whether they should proceed with certain services offered by Adobe Press. Transcribed image text: This is a graded discussion: 10 points possible WEEK 5: AAA SERVERS Compare the relative merits of TACACS+ and RADIUS AAA servers. RADIUS stands for Remote Authentication Dial-In User Service. Pearson may disclose personal information, as follows: This web site contains links to other sites. This process is illustrated in step 2. This is an authorization level label for Kerberos principals.