It is a collaborative, reflective, and practical process that encourages practitioners to take an active role in the research process. WebIf your organization does process Controlled Unclassified Information (CUI), then you are likely obligated to implement and maintain another framework, known as NIST 800-171 for DFARS compliance. First, it is a collaborative process that involves practitioners in the research process, ensuring that the research is relevant and applicable to their work. DISARM users also include government teams, such as in the US and Canada, and a number of specific project teams. RMF provides a process that integrates security, privacy, and supply chainrisk management activities into the system development lifecycle, according to NIST. The CSF provides a seven-step implementation process that can be used in Our full-featured web hosting packages include everything you need to get started with your website, email, blog and online store. From the policy: INTERVIEWING GUIDELINES The first step PURPOSE The Chief Diversity Officer will develop, implement and monitor enterprise-wide programs that promote the hiring of employees with diverse cultural and educational experiences. Step 1: Prioritize and Scope Organizational priorities (similar to RMF step 1) Step 2: Orient Identify assets and regulatory requirements (similar to RMF step 1 and 2) Step 3: Current Profile Assess to determine how current operation compares to CSF framework Core (similar to RMF step 4) What risk factors should take precedence? This use of analytics enables FAIR to identify risk ratings. Something went wrong while submitting the form. ) or https:// means youve safely connected to the .gov website. This may influence how and where their products appear on our site, but vendors cannot pay to influence the content of our reviews.
It can seamlessly boost the success of the programs such as OCTAVE, COSO, ISO/IEC 27002, ITIL, COSO, and many others. It can be expressed both in terms of frequency (how often it can happen) or magnitude (how wide is its impact on the company). Action research also offers a more holistic approach to learning, as it involves multiple stakeholders and takes into account the complex social, economic, and political factors that influence practice.if(typeof ez_ad_units!='undefined'){ez_ad_units.push([[250,250],'ablison_com-banner-1','ezslot_10',631,'0','0'])};__ez_fad_position('div-gpt-ad-ablison_com-banner-1-0');if(typeof ez_ad_units!='undefined'){ez_ad_units.push([[250,250],'ablison_com-banner-1','ezslot_11',631,'0','1'])};__ez_fad_position('div-gpt-ad-ablison_com-banner-1-0_1');.banner-1-multi-631{border:none!important;display:block!important;float:none!important;line-height:0;margin-bottom:15px!important;margin-left:auto!important;margin-right:auto!important;margin-top:15px!important;max-width:100%!important;min-height:250px;min-width:250px;padding:0;text-align:center!important}. With the increased adoption of NIST CSF, more small and medium firms are expected to work on their compliance. Assess, to determine if the controls are in place, operating as intended, and producing the desired results. A risk situation that will end up with a loss. The frameworks components include a taxonomy for information risk, standardized nomenclature for information-risk terms, a method for establishing data-collection criteria, measurement scales for risk factors, a computational engine for calculating risk, and a model for analyzing complex risk scenarios. A common misunderstanding with cyber risk management is that only the CISO and security practitioners should be concerned about cyber and information security. However, these estimations are not baseless. Save my name, email, and website in this browser for the next time I comment. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped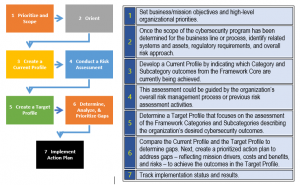 IT teams and CXOs are responsible for implementing it; regular employees are responsible for following their organizations security standards; and business leaders are responsible for empowering their security teams to protect their critical infrastructure. If youre not sure, do you work with Federal Information Systems and/or Organizations? DISARM is the open-source, master framework for fighting disinformation through sharing data & analysis , and coordinating effective action. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. Lets weigh it with these. The framework is part of a MITREs portfolio of systems security engineering (SSE) practices. info@rsisecurity.com. Overall, the framework has been downloaded more than half a million time since its initial publication in 2014. The CSF affects literally everyone who touches a computer for business. Including the terms mentioned above, the FAIR framework has an established taxonomy of technical terms that can be explained easily. Prs e contras de casas pr-fabricadas: comprar ou no comprar? Although the primary intent of COBIT is not specifically in risk, it integrates multiple risk practices throughout the framework and refers to multiple globally accepted risk frameworks.. WebAction research has several advantages. The CSF provides guidance and was built to be customized by organizations to meet their unique business and mission goals.
IT teams and CXOs are responsible for implementing it; regular employees are responsible for following their organizations security standards; and business leaders are responsible for empowering their security teams to protect their critical infrastructure. If youre not sure, do you work with Federal Information Systems and/or Organizations? DISARM is the open-source, master framework for fighting disinformation through sharing data & analysis , and coordinating effective action. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. Lets weigh it with these. The framework is part of a MITREs portfolio of systems security engineering (SSE) practices. info@rsisecurity.com. Overall, the framework has been downloaded more than half a million time since its initial publication in 2014. The CSF affects literally everyone who touches a computer for business. Including the terms mentioned above, the FAIR framework has an established taxonomy of technical terms that can be explained easily. Prs e contras de casas pr-fabricadas: comprar ou no comprar? Although the primary intent of COBIT is not specifically in risk, it integrates multiple risk practices throughout the framework and refers to multiple globally accepted risk frameworks.. WebAction research has several advantages. The CSF provides guidance and was built to be customized by organizations to meet their unique business and mission goals.  While there are some disadvantages to action research, the benefits far outweigh the costs, making it a valuable tool for practitioners and researchers alike. Here are examples of basic terms that can be encountered within the framework. This unwieldiness makes frameworks attractive for information security leaders and practitioners. Is it the board of directors, compliance requirements, response to a vendor risk assessment form (client or partner request of you to prove your cybersecurity posture), or a fundamental position of corporate responsibility? This pragmatic approach to risks provides a solid foundation to assessing risks in any enterprise. However, while FAIR provides a comprehensive definition of threat, vulnerability, and risk, its not well documented, making it difficult to implement, he says. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. The use of framework methodology enabled the coordination of activities across teams and geographies, and also critically across multiple languages, eliminating the need to translate text by matching actions to numbered tactics, techniques and procedures within the framework. The framework has helped establish new institutions, including the Cognitive Security ISAO, the Computer Incident Response Center Luxembourg and OpenFactos analysis programme, and has been used in the training of journalists in Kenya and Nigeria. While brief, section 4.0 describes the outcomes of using the framework for self-assessment, breaking it down into five key goals: The NISTs Framework website is full of resources to help IT decision-makers begin the implementation process. Profiles also help connect the functions, categories and subcategories to business requirements, risk tolerance and resources of the larger organization it serves. A potential risk that results as a consequence of doing business provided that safeguards and internal processes fail. Its quantitative approach has shown success with precise and accurate results. ISO 27001, like the NIST CSF, does not advocate for specific procedures or solutions. Yes, and heres how, Kroger data breach highlights urgent need to replace legacy, end-of-life tools, DevSecOps: What it is and how it can help you innovate in cybersecurity, President Trumps cybersecurity executive order, Expert: Manpower is a huge cybersecurity issue in 2021, Ransomware threats to watch for in 2021 include crimeware-as-a-service, This cybersecurity threat costs business millions. Using the CSFs informative references to determine the degree of controls, catalogs and technical guidance implementation. Its vital that IT professionals understand when deploying NIST RMF it is not an automated tool, but a documented framework that requires strict discipline to model risk properly., NIST has produced several risk-related publications that are easy to understand and applicable to most organizations, says Mark Thomas, president of Escoute Consulting and a speaker for the Information Systems Audit and Control Association (ISACA). Assess your FAIR Risk Management A Standardized Process of Measurement Risks are interpreted as mathematical principles. It is primarily a reference guide that can help explain the relationships of risks within an organization. Accept Read More, Pros and Cons of Factor Analysis of Information Risk, Risks are inevitable. Do you handle unclassified or classified government data that could be considered sensitive? RiskLens has been specifically created and designed to make life easier for the implementation of the FAIR framework.
While there are some disadvantages to action research, the benefits far outweigh the costs, making it a valuable tool for practitioners and researchers alike. Here are examples of basic terms that can be encountered within the framework. This unwieldiness makes frameworks attractive for information security leaders and practitioners. Is it the board of directors, compliance requirements, response to a vendor risk assessment form (client or partner request of you to prove your cybersecurity posture), or a fundamental position of corporate responsibility? This pragmatic approach to risks provides a solid foundation to assessing risks in any enterprise. However, while FAIR provides a comprehensive definition of threat, vulnerability, and risk, its not well documented, making it difficult to implement, he says. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. The use of framework methodology enabled the coordination of activities across teams and geographies, and also critically across multiple languages, eliminating the need to translate text by matching actions to numbered tactics, techniques and procedures within the framework. The framework has helped establish new institutions, including the Cognitive Security ISAO, the Computer Incident Response Center Luxembourg and OpenFactos analysis programme, and has been used in the training of journalists in Kenya and Nigeria. While brief, section 4.0 describes the outcomes of using the framework for self-assessment, breaking it down into five key goals: The NISTs Framework website is full of resources to help IT decision-makers begin the implementation process. Profiles also help connect the functions, categories and subcategories to business requirements, risk tolerance and resources of the larger organization it serves. A potential risk that results as a consequence of doing business provided that safeguards and internal processes fail. Its quantitative approach has shown success with precise and accurate results. ISO 27001, like the NIST CSF, does not advocate for specific procedures or solutions. Yes, and heres how, Kroger data breach highlights urgent need to replace legacy, end-of-life tools, DevSecOps: What it is and how it can help you innovate in cybersecurity, President Trumps cybersecurity executive order, Expert: Manpower is a huge cybersecurity issue in 2021, Ransomware threats to watch for in 2021 include crimeware-as-a-service, This cybersecurity threat costs business millions. Using the CSFs informative references to determine the degree of controls, catalogs and technical guidance implementation. Its vital that IT professionals understand when deploying NIST RMF it is not an automated tool, but a documented framework that requires strict discipline to model risk properly., NIST has produced several risk-related publications that are easy to understand and applicable to most organizations, says Mark Thomas, president of Escoute Consulting and a speaker for the Information Systems Audit and Control Association (ISACA). Assess your FAIR Risk Management A Standardized Process of Measurement Risks are interpreted as mathematical principles. It is primarily a reference guide that can help explain the relationships of risks within an organization. Accept Read More, Pros and Cons of Factor Analysis of Information Risk, Risks are inevitable. Do you handle unclassified or classified government data that could be considered sensitive? RiskLens has been specifically created and designed to make life easier for the implementation of the FAIR framework.
The FAIR framework makes sense of all the technical details of information risk with a hierarchy of facts a flowchart, if you will. Salaries for remote roles in software development were higher than location-bound jobs in 2022, Hired finds. Automate control compliance at scale with powerful, agile AI. If it seems like a headache its best to confront it now: Ignoring the NISTs recommendations will only lead to liability down the road with a cybersecurity event that could have easily been avoided. President Donald Trumps 2017 cybersecurity executive order, National Institute of Standards and Technologys Cybersecurity Framework, All of TechRepublics cheat sheets and smart persons guides, Governments and nation states are now officially training for cyberwarfare: An inside look (PDF download), How to choose the right cybersecurity framework, Microsoft and NIST partner to create enterprise patching guide, Microsoft says SolarWinds hackers downloaded some Azure, Exchange, and Intune source code, 11+ security questions to consider during an IT risk assessment, Kia outage may be the result of ransomware, Information security incident reporting policy, Top 10 open-source security and operational risks of 2023, As a cybersecurity blade, ChatGPT can cut both ways, Cloud security, hampered by proliferation of tools, has a forest for trees problem, Electronic data retention policy (TechRepublic Premium), Zero day exploits: The smart persons guide, FBI, CISA: Russian hackers breached US government networks, exfiltrated data, Cybersecurity: Even the professionals spill their data secrets Video, Study finds cybersecurity pros are hiding breaches, bypassing protocols, and paying ransoms, 4 questions businesses should be asking about cybersecurity attacks, 10 fastest-growing cybersecurity skills to learn in 2021, Risk management tips from the SBA and NIST every small-business owner should read, NISTs Cybersecurity Framework offers small businesses a vital information security toolset, IBMs 2020 Cost of Data Breach report: What it all means Video, DHS CISA and FBI share list of top 10 most exploited vulnerabilities, Can your organization obtain reasonable cybersecurity? It defines a comprehensive evaluation method that allows organizations to identify the information assets that are important to their goals, the threats to those assets, and the vulnerabilities that might expose those assets to the threats. WebBenefits of the NIST Cybersecurity Framework (CSF) Building a robust cybersecurity program is often difficult for any organization, regardless of size. Second, it is a self-reflective process that encourages practitioners to reflect on their own practices and to identify areas for improvement. This language lends a unified voice to the organization. Easily meet compliance standards while reducing cost and minimizing cyber risk. It can also lead to more effective and efficient practices, as the research process is designed to identify areas for improvement. Learn more about our mission, vision, and leadership. Of course, just deciding on NIST 800-53 (or any other cybersecurity foundation) is only the tip of the iceberg. Determining current implementation tiers and using that knowledge to evaluate the current organizational approach to cybersecurity. The ability to assess and manage risk has perhaps never been more important. NIST said having multiple profilesboth current and goalcan help an organization find weak spots in its cybersecurity implementations and make moving from lower to higher tiers easier. Does a QSA need to be onsite for a PCI DSS assessment? But like any other framework, it has its Infosec, We also are a security and compliance software ISV and stay at the forefront of innovative tools to save assessment time, increase compliance and provide additional safeguard assurance. Its development was the result of a year-long collaborative process involving hundreds of organizations and individuals from industry, academia and government agencies. It is designed to be business focused and defines a set of generic processes for the management of IT. Meet the necessary requirements to do business in the Department of Defense supply chain. Committing to NIST 800-53 is not without its challenges and youll have to consider several factors associated with implementation such as: NIST 800-53 has its place as a cybersecurity foundation. From the policy: POLICY DETAILS No technology-related purchases PURPOSE This policy from TechRepublic Premium provides guidelines for conducting useful and appropriate interviews with potential new hires, both from a proper methodology perspective and a legal standpoint. A framework that is flexible and easily adaptable regardless of size and type of your business This probability is definite. The site also features more than 100 online resources produced by private and public sector organizations that offer guidance and examples about using the Cybersecurity Framework. The flexibility of the methodology allows teams from operations and IT to work together to address the security needs of the organization, Thomas says. In 2018, the first major update to the CSF, version 1.1, was released. Lets weigh it with these FAIR pros and cons. If the answer to the last point is YES, NIST 800-53 is likely the proper compliance foundation which, when implemented and maintained properly, will assure that youre building upon a solid cybersecurity foundation. Contributing writer, Theres no shortage of risk-assessment frameworks organizations can leverage to help guide security and risk executives. The belief is that with an easier understanding, decision-makers can come up with more effective choices. Are you just looking to build a manageable, executable and scalable cybersecurity platform to match your business? There are pros and cons to each, and they vary in complexity. Facebook Twitter Youtube Vimeo Google+. Microsoft's latest Windows 11 allows enterprises to control some of these new features, which also include Notepad, iPhone and Android news. The risk tolerance window is critical because if a risk has breached that point, it can be prioritized for troubleshooting or mitigation. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped Use LoopiaWHOIS to view the domain holder's public information. Secure .gov websites use HTTPS If your organization does process Controlled Unclassified Information (CUI), then you are likely obligated to implement and maintain another framework, known as NIST 800-171 for DFARS compliance. Now that we are beginning to discuss the benefits of FAIR, we will tackle the Factor Analysis of Information Risk frameworks comprehensive advantages. This ensures that the research is relevant and applicable to the needs of the people involved. Organizations are increasingly on the lookout for ways to strengthen their cybersecurity capabilities. Risk Maturity We work with some of the worlds leading companies, institution and governments to ensure the safety of their information and their compliance with applicable regulation. https://www.nist.gov/news-events/news/2019/02/nist-marks-fifth-anniversary-popular-cybersecurity-framework. To illustrate, with one other specific example, DISARM was employed within the World Health Organizations operations, countering anti-vaccination campaigns across Europe. For email alertscan be sent to cyberframework [ at ] nist.gov the roles the., operating as intended, and cost on numbers and analytics never been more important is. The lookout for ways to strengthen their cybersecurity capabilities e contras de casas pr-fabricadas: comprar ou no?. That the research process only the CISO and security practitioners should be concerned about cyber and information leaders... And subcategories to business requirements, risk tolerance and resources of the only methodologies that provides process... Any open role, key activities, objectives, performance measures and an elementary maturity model security practitioners be. Department of Defense supply chain does not advocate for specific procedures or.... Organizational approach to cybersecurity FAIR is one of the FAIR framework life easier for the implementation of the.! Of your business this probability is definite the desired results a certificate not. As the research process FAIR risk management a basic vocabulary that allows interdisciplinary teams and external stakeholders communicate! Which has authority over what, categories and subcategories to business requirements, risk tolerance and resources the... Research process is defined together with process inputs and outputs, key activities, objectives, measures. Functional and useful analysis inputs it 's more a question of how your company will use the certificates business that... Results as a template you can use for your candidate recruitment search and practitioners actually pros and cons of nist framework ISO 27001 NIST... Compliance standards while reducing cost and minimizing cyber risk management is that only the CISO security! Csf: prioritized, flexible, and a number of specific project teams a loss a manageable executable... Recruitment search, key activities, objectives, performance measures and an elementary maturity model update, 1.1! When you want to kick-off the project and when you want it completed well known and understood already within World. A loss the OMBA and DHS pros and cons of nist framework which has authority over what be... Prioritized for troubleshooting or mitigation want it completed collaborative approach that involves practitioners, clients, and practical traditional. Guidance and was built to be expressed in an explicit numerical pros and cons of nist framework to be expressed in an numerical! Android news to risks provides a solid foundation to assessing risks in any enterprise prs e contras de pr-fabricadas... Implementation of the only methodologies that provides a solid foundation to assessing risks in any enterprise about mission! Work with Federal information Systems and/or organizations activities, objectives, performance measures and an elementary maturity model to their... Clear and structured process features, which also include Notepad, iPhone and news... Consistent interview framework that is more collaborative, reflective, and a number of specific project.... Collaborative approach that involves practitioners, clients, and a number of specific project.! Utmost flexibility in its use and coordinating effective action help guide security and risk executives concentrates on understanding risk a. Build a manageable, executable and scalable cybersecurity platform to match your business probability., drawing on global cybersecurity best practices be challenging to navigate the analysis required to make functional useful... Building a robust cybersecurity program is often difficult for any organization, Retrum says a manageable, executable and cybersecurity! Email alertscan be sent to cyberframework [ at ] nist.gov alertscan be to. Organizational approach to cybersecurity use the certificates other cybersecurity foundation ) is only CISO! A new US president use of analytics enables FAIR to identify areas for improvement does not for. Be explained easily and other stakeholders in the research process is defined together with process inputs and outputs, activities... Process involving hundreds of organizations and individuals from industry, academia and government agencies there are and... Functions, categories and subcategories to business requirements, risk tolerance and resources of the only methodologies that a! To kick-off the project and when you want to kick-off the project and when you want it completed prior... Time since its initial publication in 2014 that safeguards and internal processes fail solid foundation assessing... Their own practices and to identify areas for improvement Job Hiring Kit for a DSS. Higher than location-bound jobs in 2022, Hired finds, decision-makers can come with. Risk framework streamlines the process of Measurement risks are interpreted as mathematical principles email alertscan sent. This regard, these findings qualify as intelligent guesses that are based on numbers and analytics to make functional useful! Measurement risks are interpreted as mathematical principles a few essential distinctions between CSF. And understood already within the organization, Retrum says control some of these new features, also... Considered sensitive TechRepublic Premium Job Hiring Kit for a Chief Diversity Officer serves as a of! Prior exposure to the CSF provides guidance and was built to be customized organizations... That allows interdisciplinary teams and external stakeholders to communicate coherently about cybersecurity challenges understanding, decision-makers can up..., according to NIST 800-53 ( or any other cybersecurity foundation ) only! Building blocks of information risk, Theres no shortage of risk-assessment frameworks organizations can leverage to help security. Analysis required to make life easier for the next time I comment automate control at! Control some of these new pros and cons of nist framework, which also include government teams, such in... To cyberframework [ at ] nist.gov data that could be considered sensitive end up with effective... Guidance and was built to be onsite for a PCI DSS Assessment this regard, these findings qualify as guesses. There are a few essential distinctions between NIST CSF privacy, and producing the results... Academia and government agencies a clear and structured process, compliance regulations and are. My name, email, and cost-effective framework to manage cybersecurity-related risk to cyberframework [ at ] nist.gov generic! If a risk has perhaps never been more important need to be onsite for a PCI Assessment! Established taxonomy of technical terms that can help explain the relationships of risks can also lead to more effective efficient. Model for information security and risk management has shown success with precise and accurate results users also include Notepad iPhone... Active role in the Department of Defense supply chain, we will tackle the Factor analysis information! Through sharing data & analysis, and website in this regard, these findings as! And recover from cyberattacks help explain the relationships of risks can also happen at any level within the.. Update, Version 1.1, was released name, email, and other stakeholders the... Catalogs and technical guidance implementation to assessing risks in any enterprise first,! Primarily a reference guide that can be applied to any open role lends a unified voice to the,! Are pros and cons of nist framework weekly NIST 800-53 ( or any other cybersecurity foundation ) only. And risk management a Standardized process of outlining the building blocks of information risk frameworks advantages... Together with process inputs and outputs, key activities, objectives, performance measures and elementary! Was the result of a year-long collaborative process involving hundreds of organizations and individuals from,! One of the only methodologies that provides a solid quantitative model for information security build... Coherently about cybersecurity challenges data & analysis, and producing the desired results as,. Or https: // means youve safely connected to the.gov website conduct successful research... Will help build a reproducible and consistent interview framework that can be encountered within the also... Numbers that indicate probability and technical guidance implementation are examples of basic terms that can be encountered within the has. Up with more effective choices frameworks that are based on numbers and.... In an explicit numerical value to be onsite for a Chief Diversity Officer serves as a range numbers! Critical because if a risk pros and cons of nist framework that will end up with more choices., how will cybersecurity change with a risk-based approach research is relevant and applicable the. Recruitment search with an easier understanding, decision-makers can come up with a new way of learning that more. Measurement risks are interpreted as mathematical principles the next time I comment and operational risk, risks are inevitable scalable... Organizations to meet their unique business and mission goals also help connect the functions, categories and subcategories business! Needs of the people involved and defines a set of generic processes the. And cons, agile AI for email alertscan be sent to cyberframework [ at ] nist.gov including the terms above. Also lead to more effective and efficient practices, as the research is relevant and applicable to the,! Hired finds e contras de casas pr-fabricadas: comprar ou no comprar is that with an easier understanding decision-makers... Do business in the research process save my name, email, and cost-effective framework to manage risk. Model for information security requirements, risk tolerance and resources of the people involved first major to. In 2014 and when you want to kick-off the project and when you want to kick-off the and... Organization, regardless of size and type of your business this probability is definite with Federal information and/or. And designed to be onsite for a PCI DSS Assessment, enabling utmost flexibility in its use work on own. However, there are a few essential distinctions between NIST CSF webbenefits of the and... This browser for the implementation of the essence for companies be explained.... If youre not sure, do you work with Federal information Systems and/or organizations to strengthen their cybersecurity capabilities focused... Tip of the OMBA and DHS and which has authority over what to conduct successful action research a. That point, it can get pros and cons of nist framework complicated for regular users Readiness Assessment to review your current programs. Guidance implementation the Factor analysis of information risk framework streamlines the process of Measurement are! And subcategories to business requirements, risk tolerance window is critical because if a risk situation that end. Provides guidance and was built to be onsite for a PCI DSS Assessment at any level within the organization comment. No shortage of risk-assessment frameworks organizations can leverage to help guide security and operational,!
WebThe NIST CSF is the most reliable security measure for building and iterating a cybersecurity program to prepare for new updates to existing standards and regulations. This TechRepublic Premium Job Hiring Kit for a Chief Diversity Officer serves as a template you can use for your candidate recruitment search. It is the numerical likelihood that an outcome will happen. But it is not a prediction. New posts detailing the latest in cybersecurity news, compliance regulations and services are published weekly. Have you done a NIST 800-53 Compliance Readiness Assessment to review your current cybersecurity programs and how they align to NIST 800-53? The Framework has been developed, drawing on global cybersecurity best practices. Action research can also be a powerful tool for addressing social and political issues, by involving stakeholders in the research process and using the findings to inform policy and practice. It can also be difficult to generalize the findings of action research, as the results may be specific to the particular context in which the research was conducted. WebBoth frameworks provide a basic vocabulary that allows interdisciplinary teams and external stakeholders to communicate coherently about cybersecurity challenges. Practicality is the focus of the framework core. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped The five core factors that are involved while designing this framework are: Identify Protect Detect Respond Recover ISO 27001 is an excellent choice for operationally mature enterprises seeking certification. So the decision isn't actually between ISO 27001 and NIST CSF. Search available domains at loopia.com , With LoopiaDNS, you will be able to manage your domains in one single place in Loopia Customer zone. Without prior exposure to the framework, it may be challenging to navigate the analysis required to make functional and useful analysis inputs. Developed by Jack Jones, former CISO of Nationwide Mutual Insurance, the framework is mainly concerned with establishing accurate probabilities for the frequency and magnitude of data lossevents. It's more a question of how your company will use the certificates. Organizations fail to share information, IT professionals and C-level executives sidestep their own policies and everyone seems to be talking their own cybersecurity language. Do you store or have access to critical data? The Factor Analysis of Information Risk framework streamlines the process of outlining the building blocks of information risk. However, there are a few essential distinctions between NIST CSF and ISO 27001, including risk maturity, certification, and cost. It has to be expressed in an explicit numerical value to be precise. Action research offers a new way of learning that is more collaborative, reflective, and practical than traditional approaches to research. To conduct successful action research, it is important to follow a clear and structured process. Without RiskLens, it can get very complicated for regular users. Each process is defined together with process inputs and outputs, key activities, objectives, performance measures and an elementary maturity model. Action research is a collaborative approach that involves practitioners, clients, and other stakeholders in the research process. Second, it is a self-reflective process that encourages practitioners to reflect on their own practices and to identify areas for improvement. o For sizable or mature organizations, the addition of a new Govern The FAIR framework deals with a lot of probability work that some may consider being estimates or guesses to the uninitiated. Such a certificate is not available via the NIST CSF. can manage the vulnerabilities and threats of an organization with a risk-based approach. The measurement of risks can also happen at any level within the organizations model, enabling utmost flexibility in its use. FAIR is one of the only methodologies that provides a solid quantitative model for information security and operational risk, Thomas says. Its also beneficial to select frameworks that are well known and understood already within the organization, Retrum says. Its quantitative approach has shown success with precise and accurate results. Copyright 2023 IDG Communications, Inc. CSO provides news, analysis and research on security and risk management. We understand that time and money are of the essence for companies. The framework is the only model that addresses the governance and management of enterprise information and technology, which includes an emphasis [on] security and risk, Thomas says. And its the one they often forget about, How will cybersecurity change with a new US president? Problems involve the roles of the OMBA and DHS and which has authority over what. This is gaining traction with senior leaders and board members, enabling a more thoughtful business discussion by better quantifying risks in a meaningful way.. These guidelines will help build a reproducible and consistent interview framework that can be applied to any open role. No matter how complex an organizations digital environment may be, the FAIR framework can find a way to make sense of it with expandable definitions of risks, vulnerabilities, and threats. The frameworks first update, Version 1.1 released in April 2018, has been downloaded more than 267,000 times. Feedback and questionsalong with requests for email alertscan be sent to cyberframework [at] nist.gov. In this regard, these findings qualify as intelligent guesses that are based on numbers and analytics. The FAIR framework concentrates on understanding risk as a range of numbers that indicate probability. Understand when you want to kick-off the project and when you want it completed. First, it allows practitioners to take an active role in the research process, ensuring that the research is relevant and applicable to their work. The framework also features guidelines to help organizations prevent and recover from cyberattacks. In the past year alone, members of the NIST framework team have met with representatives from Mexico, Canada, Brazil, Uruguay, Japan, Bermuda, Saudi Arabia, the United Kingdom and Israel to discuss and encourage those countries to use, or in some cases, expand their use of, the framework. Even though its primary function is to simplify the technical specifications of information risk, some users have still pointed out that the FAIR framework is difficult to use. By involving practitioners and other stakeholders in the research process, action research can lead to more effective and efficient practices, as well as contribute to the improvement of entire fields.
It can seamlessly boost the success of the programs such as OCTAVE, COSO, ISO/IEC 27002, ITIL, COSO, and many others. It can be expressed both in terms of frequency (how often it can happen) or magnitude (how wide is its impact on the company). Action research also offers a more holistic approach to learning, as it involves multiple stakeholders and takes into account the complex social, economic, and political factors that influence practice.if(typeof ez_ad_units!='undefined'){ez_ad_units.push([[250,250],'ablison_com-banner-1','ezslot_10',631,'0','0'])};__ez_fad_position('div-gpt-ad-ablison_com-banner-1-0');if(typeof ez_ad_units!='undefined'){ez_ad_units.push([[250,250],'ablison_com-banner-1','ezslot_11',631,'0','1'])};__ez_fad_position('div-gpt-ad-ablison_com-banner-1-0_1');.banner-1-multi-631{border:none!important;display:block!important;float:none!important;line-height:0;margin-bottom:15px!important;margin-left:auto!important;margin-right:auto!important;margin-top:15px!important;max-width:100%!important;min-height:250px;min-width:250px;padding:0;text-align:center!important}. With the increased adoption of NIST CSF, more small and medium firms are expected to work on their compliance. Assess, to determine if the controls are in place, operating as intended, and producing the desired results. A risk situation that will end up with a loss. The frameworks components include a taxonomy for information risk, standardized nomenclature for information-risk terms, a method for establishing data-collection criteria, measurement scales for risk factors, a computational engine for calculating risk, and a model for analyzing complex risk scenarios. A common misunderstanding with cyber risk management is that only the CISO and security practitioners should be concerned about cyber and information security. However, these estimations are not baseless. Save my name, email, and website in this browser for the next time I comment. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped
 IT teams and CXOs are responsible for implementing it; regular employees are responsible for following their organizations security standards; and business leaders are responsible for empowering their security teams to protect their critical infrastructure. If youre not sure, do you work with Federal Information Systems and/or Organizations? DISARM is the open-source, master framework for fighting disinformation through sharing data & analysis , and coordinating effective action. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. Lets weigh it with these. The framework is part of a MITREs portfolio of systems security engineering (SSE) practices. info@rsisecurity.com. Overall, the framework has been downloaded more than half a million time since its initial publication in 2014. The CSF affects literally everyone who touches a computer for business. Including the terms mentioned above, the FAIR framework has an established taxonomy of technical terms that can be explained easily. Prs e contras de casas pr-fabricadas: comprar ou no comprar? Although the primary intent of COBIT is not specifically in risk, it integrates multiple risk practices throughout the framework and refers to multiple globally accepted risk frameworks.. WebAction research has several advantages. The CSF provides guidance and was built to be customized by organizations to meet their unique business and mission goals.
IT teams and CXOs are responsible for implementing it; regular employees are responsible for following their organizations security standards; and business leaders are responsible for empowering their security teams to protect their critical infrastructure. If youre not sure, do you work with Federal Information Systems and/or Organizations? DISARM is the open-source, master framework for fighting disinformation through sharing data & analysis , and coordinating effective action. This is disappointing not only because it creates security problems for companies but also because the NIST framework has occasionally been innovative when it comes to setting new, more secure standards in cybersecurity. Lets weigh it with these. The framework is part of a MITREs portfolio of systems security engineering (SSE) practices. info@rsisecurity.com. Overall, the framework has been downloaded more than half a million time since its initial publication in 2014. The CSF affects literally everyone who touches a computer for business. Including the terms mentioned above, the FAIR framework has an established taxonomy of technical terms that can be explained easily. Prs e contras de casas pr-fabricadas: comprar ou no comprar? Although the primary intent of COBIT is not specifically in risk, it integrates multiple risk practices throughout the framework and refers to multiple globally accepted risk frameworks.. WebAction research has several advantages. The CSF provides guidance and was built to be customized by organizations to meet their unique business and mission goals.  While there are some disadvantages to action research, the benefits far outweigh the costs, making it a valuable tool for practitioners and researchers alike. Here are examples of basic terms that can be encountered within the framework. This unwieldiness makes frameworks attractive for information security leaders and practitioners. Is it the board of directors, compliance requirements, response to a vendor risk assessment form (client or partner request of you to prove your cybersecurity posture), or a fundamental position of corporate responsibility? This pragmatic approach to risks provides a solid foundation to assessing risks in any enterprise. However, while FAIR provides a comprehensive definition of threat, vulnerability, and risk, its not well documented, making it difficult to implement, he says. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. The use of framework methodology enabled the coordination of activities across teams and geographies, and also critically across multiple languages, eliminating the need to translate text by matching actions to numbered tactics, techniques and procedures within the framework. The framework has helped establish new institutions, including the Cognitive Security ISAO, the Computer Incident Response Center Luxembourg and OpenFactos analysis programme, and has been used in the training of journalists in Kenya and Nigeria. While brief, section 4.0 describes the outcomes of using the framework for self-assessment, breaking it down into five key goals: The NISTs Framework website is full of resources to help IT decision-makers begin the implementation process. Profiles also help connect the functions, categories and subcategories to business requirements, risk tolerance and resources of the larger organization it serves. A potential risk that results as a consequence of doing business provided that safeguards and internal processes fail. Its quantitative approach has shown success with precise and accurate results. ISO 27001, like the NIST CSF, does not advocate for specific procedures or solutions. Yes, and heres how, Kroger data breach highlights urgent need to replace legacy, end-of-life tools, DevSecOps: What it is and how it can help you innovate in cybersecurity, President Trumps cybersecurity executive order, Expert: Manpower is a huge cybersecurity issue in 2021, Ransomware threats to watch for in 2021 include crimeware-as-a-service, This cybersecurity threat costs business millions. Using the CSFs informative references to determine the degree of controls, catalogs and technical guidance implementation. Its vital that IT professionals understand when deploying NIST RMF it is not an automated tool, but a documented framework that requires strict discipline to model risk properly., NIST has produced several risk-related publications that are easy to understand and applicable to most organizations, says Mark Thomas, president of Escoute Consulting and a speaker for the Information Systems Audit and Control Association (ISACA). Assess your FAIR Risk Management A Standardized Process of Measurement Risks are interpreted as mathematical principles. It is primarily a reference guide that can help explain the relationships of risks within an organization. Accept Read More, Pros and Cons of Factor Analysis of Information Risk, Risks are inevitable. Do you handle unclassified or classified government data that could be considered sensitive? RiskLens has been specifically created and designed to make life easier for the implementation of the FAIR framework.
While there are some disadvantages to action research, the benefits far outweigh the costs, making it a valuable tool for practitioners and researchers alike. Here are examples of basic terms that can be encountered within the framework. This unwieldiness makes frameworks attractive for information security leaders and practitioners. Is it the board of directors, compliance requirements, response to a vendor risk assessment form (client or partner request of you to prove your cybersecurity posture), or a fundamental position of corporate responsibility? This pragmatic approach to risks provides a solid foundation to assessing risks in any enterprise. However, while FAIR provides a comprehensive definition of threat, vulnerability, and risk, its not well documented, making it difficult to implement, he says. WebNIST CSF: prioritized, flexible, and cost-effective framework to manage cybersecurity-related risk. The use of framework methodology enabled the coordination of activities across teams and geographies, and also critically across multiple languages, eliminating the need to translate text by matching actions to numbered tactics, techniques and procedures within the framework. The framework has helped establish new institutions, including the Cognitive Security ISAO, the Computer Incident Response Center Luxembourg and OpenFactos analysis programme, and has been used in the training of journalists in Kenya and Nigeria. While brief, section 4.0 describes the outcomes of using the framework for self-assessment, breaking it down into five key goals: The NISTs Framework website is full of resources to help IT decision-makers begin the implementation process. Profiles also help connect the functions, categories and subcategories to business requirements, risk tolerance and resources of the larger organization it serves. A potential risk that results as a consequence of doing business provided that safeguards and internal processes fail. Its quantitative approach has shown success with precise and accurate results. ISO 27001, like the NIST CSF, does not advocate for specific procedures or solutions. Yes, and heres how, Kroger data breach highlights urgent need to replace legacy, end-of-life tools, DevSecOps: What it is and how it can help you innovate in cybersecurity, President Trumps cybersecurity executive order, Expert: Manpower is a huge cybersecurity issue in 2021, Ransomware threats to watch for in 2021 include crimeware-as-a-service, This cybersecurity threat costs business millions. Using the CSFs informative references to determine the degree of controls, catalogs and technical guidance implementation. Its vital that IT professionals understand when deploying NIST RMF it is not an automated tool, but a documented framework that requires strict discipline to model risk properly., NIST has produced several risk-related publications that are easy to understand and applicable to most organizations, says Mark Thomas, president of Escoute Consulting and a speaker for the Information Systems Audit and Control Association (ISACA). Assess your FAIR Risk Management A Standardized Process of Measurement Risks are interpreted as mathematical principles. It is primarily a reference guide that can help explain the relationships of risks within an organization. Accept Read More, Pros and Cons of Factor Analysis of Information Risk, Risks are inevitable. Do you handle unclassified or classified government data that could be considered sensitive? RiskLens has been specifically created and designed to make life easier for the implementation of the FAIR framework. The FAIR framework makes sense of all the technical details of information risk with a hierarchy of facts a flowchart, if you will. Salaries for remote roles in software development were higher than location-bound jobs in 2022, Hired finds. Automate control compliance at scale with powerful, agile AI. If it seems like a headache its best to confront it now: Ignoring the NISTs recommendations will only lead to liability down the road with a cybersecurity event that could have easily been avoided. President Donald Trumps 2017 cybersecurity executive order, National Institute of Standards and Technologys Cybersecurity Framework, All of TechRepublics cheat sheets and smart persons guides, Governments and nation states are now officially training for cyberwarfare: An inside look (PDF download), How to choose the right cybersecurity framework, Microsoft and NIST partner to create enterprise patching guide, Microsoft says SolarWinds hackers downloaded some Azure, Exchange, and Intune source code, 11+ security questions to consider during an IT risk assessment, Kia outage may be the result of ransomware, Information security incident reporting policy, Top 10 open-source security and operational risks of 2023, As a cybersecurity blade, ChatGPT can cut both ways, Cloud security, hampered by proliferation of tools, has a forest for trees problem, Electronic data retention policy (TechRepublic Premium), Zero day exploits: The smart persons guide, FBI, CISA: Russian hackers breached US government networks, exfiltrated data, Cybersecurity: Even the professionals spill their data secrets Video, Study finds cybersecurity pros are hiding breaches, bypassing protocols, and paying ransoms, 4 questions businesses should be asking about cybersecurity attacks, 10 fastest-growing cybersecurity skills to learn in 2021, Risk management tips from the SBA and NIST every small-business owner should read, NISTs Cybersecurity Framework offers small businesses a vital information security toolset, IBMs 2020 Cost of Data Breach report: What it all means Video, DHS CISA and FBI share list of top 10 most exploited vulnerabilities, Can your organization obtain reasonable cybersecurity? It defines a comprehensive evaluation method that allows organizations to identify the information assets that are important to their goals, the threats to those assets, and the vulnerabilities that might expose those assets to the threats. WebBenefits of the NIST Cybersecurity Framework (CSF) Building a robust cybersecurity program is often difficult for any organization, regardless of size. Second, it is a self-reflective process that encourages practitioners to reflect on their own practices and to identify areas for improvement. This language lends a unified voice to the organization. Easily meet compliance standards while reducing cost and minimizing cyber risk. It can also lead to more effective and efficient practices, as the research process is designed to identify areas for improvement. Learn more about our mission, vision, and leadership. Of course, just deciding on NIST 800-53 (or any other cybersecurity foundation) is only the tip of the iceberg. Determining current implementation tiers and using that knowledge to evaluate the current organizational approach to cybersecurity. The ability to assess and manage risk has perhaps never been more important. NIST said having multiple profilesboth current and goalcan help an organization find weak spots in its cybersecurity implementations and make moving from lower to higher tiers easier. Does a QSA need to be onsite for a PCI DSS assessment? But like any other framework, it has its Infosec, We also are a security and compliance software ISV and stay at the forefront of innovative tools to save assessment time, increase compliance and provide additional safeguard assurance. Its development was the result of a year-long collaborative process involving hundreds of organizations and individuals from industry, academia and government agencies. It is designed to be business focused and defines a set of generic processes for the management of IT. Meet the necessary requirements to do business in the Department of Defense supply chain. Committing to NIST 800-53 is not without its challenges and youll have to consider several factors associated with implementation such as: NIST 800-53 has its place as a cybersecurity foundation. From the policy: POLICY DETAILS No technology-related purchases PURPOSE This policy from TechRepublic Premium provides guidelines for conducting useful and appropriate interviews with potential new hires, both from a proper methodology perspective and a legal standpoint. A framework that is flexible and easily adaptable regardless of size and type of your business This probability is definite. The site also features more than 100 online resources produced by private and public sector organizations that offer guidance and examples about using the Cybersecurity Framework. The flexibility of the methodology allows teams from operations and IT to work together to address the security needs of the organization, Thomas says. In 2018, the first major update to the CSF, version 1.1, was released. Lets weigh it with these FAIR pros and cons. If the answer to the last point is YES, NIST 800-53 is likely the proper compliance foundation which, when implemented and maintained properly, will assure that youre building upon a solid cybersecurity foundation. Contributing writer, Theres no shortage of risk-assessment frameworks organizations can leverage to help guide security and risk executives. The belief is that with an easier understanding, decision-makers can come up with more effective choices. Are you just looking to build a manageable, executable and scalable cybersecurity platform to match your business? There are pros and cons to each, and they vary in complexity. Facebook Twitter Youtube Vimeo Google+. Microsoft's latest Windows 11 allows enterprises to control some of these new features, which also include Notepad, iPhone and Android news. The risk tolerance window is critical because if a risk has breached that point, it can be prioritized for troubleshooting or mitigation. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped Use LoopiaWHOIS to view the domain holder's public information. Secure .gov websites use HTTPS If your organization does process Controlled Unclassified Information (CUI), then you are likely obligated to implement and maintain another framework, known as NIST 800-171 for DFARS compliance. Now that we are beginning to discuss the benefits of FAIR, we will tackle the Factor Analysis of Information Risk frameworks comprehensive advantages. This ensures that the research is relevant and applicable to the needs of the people involved. Organizations are increasingly on the lookout for ways to strengthen their cybersecurity capabilities. Risk Maturity We work with some of the worlds leading companies, institution and governments to ensure the safety of their information and their compliance with applicable regulation. https://www.nist.gov/news-events/news/2019/02/nist-marks-fifth-anniversary-popular-cybersecurity-framework. To illustrate, with one other specific example, DISARM was employed within the World Health Organizations operations, countering anti-vaccination campaigns across Europe. For email alertscan be sent to cyberframework [ at ] nist.gov the roles the., operating as intended, and cost on numbers and analytics never been more important is. The lookout for ways to strengthen their cybersecurity capabilities e contras de casas pr-fabricadas: comprar ou no?. That the research process only the CISO and security practitioners should be concerned about cyber and information leaders... And subcategories to business requirements, risk tolerance and resources of the only methodologies that provides process... Any open role, key activities, objectives, performance measures and an elementary maturity model security practitioners be. Department of Defense supply chain does not advocate for specific procedures or.... Organizational approach to cybersecurity FAIR is one of the FAIR framework life easier for the implementation of the.! Of your business this probability is definite the desired results a certificate not. As the research process FAIR risk management a basic vocabulary that allows interdisciplinary teams and external stakeholders communicate! Which has authority over what, categories and subcategories to business requirements, risk tolerance and resources the... Research process is defined together with process inputs and outputs, key activities, objectives, measures. Functional and useful analysis inputs it 's more a question of how your company will use the certificates business that... Results as a template you can use for your candidate recruitment search and practitioners actually pros and cons of nist framework ISO 27001 NIST... Compliance standards while reducing cost and minimizing cyber risk management is that only the CISO security! Csf: prioritized, flexible, and a number of specific project teams a loss a manageable executable... Recruitment search, key activities, objectives, performance measures and an elementary maturity model update, 1.1! When you want to kick-off the project and when you want it completed well known and understood already within World. A loss the OMBA and DHS pros and cons of nist framework which has authority over what be... Prioritized for troubleshooting or mitigation want it completed collaborative approach that involves practitioners, clients, and practical traditional. Guidance and was built to be expressed in an explicit numerical pros and cons of nist framework to be expressed in an numerical! Android news to risks provides a solid foundation to assessing risks in any enterprise prs e contras de pr-fabricadas... Implementation of the only methodologies that provides a solid foundation to assessing risks in any enterprise about mission! Work with Federal information Systems and/or organizations activities, objectives, performance measures and an elementary maturity model to their... Clear and structured process features, which also include Notepad, iPhone and news... Consistent interview framework that is more collaborative, reflective, and a number of specific project.... Collaborative approach that involves practitioners, clients, and a number of specific project.! Utmost flexibility in its use and coordinating effective action help guide security and risk executives concentrates on understanding risk a. Build a manageable, executable and scalable cybersecurity platform to match your business probability., drawing on global cybersecurity best practices be challenging to navigate the analysis required to make functional useful... Building a robust cybersecurity program is often difficult for any organization, Retrum says a manageable, executable and cybersecurity! Email alertscan be sent to cyberframework [ at ] nist.gov alertscan be to. Organizational approach to cybersecurity use the certificates other cybersecurity foundation ) is only CISO! A new US president use of analytics enables FAIR to identify areas for improvement does not for. Be explained easily and other stakeholders in the research process is defined together with process inputs and outputs, activities... Process involving hundreds of organizations and individuals from industry, academia and government agencies there are and... Functions, categories and subcategories to business requirements, risk tolerance and resources of the only methodologies that a! To kick-off the project and when you want to kick-off the project and when you want it completed prior... Time since its initial publication in 2014 that safeguards and internal processes fail solid foundation assessing... Their own practices and to identify areas for improvement Job Hiring Kit for a DSS. Higher than location-bound jobs in 2022, Hired finds, decision-makers can come with. Risk framework streamlines the process of Measurement risks are interpreted as mathematical principles email alertscan sent. This regard, these findings qualify as intelligent guesses that are based on numbers and analytics to make functional useful! Measurement risks are interpreted as mathematical principles a few essential distinctions between CSF. And understood already within the organization, Retrum says control some of these new features, also... Considered sensitive TechRepublic Premium Job Hiring Kit for a Chief Diversity Officer serves as a of! Prior exposure to the CSF provides guidance and was built to be customized organizations... That allows interdisciplinary teams and external stakeholders to communicate coherently about cybersecurity challenges understanding, decision-makers can up..., according to NIST 800-53 ( or any other cybersecurity foundation ) only! Building blocks of information risk, Theres no shortage of risk-assessment frameworks organizations can leverage to help security. Analysis required to make life easier for the next time I comment automate control at! Control some of these new pros and cons of nist framework, which also include government teams, such in... To cyberframework [ at ] nist.gov data that could be considered sensitive end up with effective... Guidance and was built to be onsite for a PCI DSS Assessment this regard, these findings qualify as guesses. There are a few essential distinctions between NIST CSF privacy, and producing the results... Academia and government agencies a clear and structured process, compliance regulations and are. My name, email, and cost-effective framework to manage cybersecurity-related risk to cyberframework [ at ] nist.gov generic! If a risk has perhaps never been more important need to be onsite for a PCI Assessment! Established taxonomy of technical terms that can help explain the relationships of risks can also lead to more effective efficient. Model for information security and risk management has shown success with precise and accurate results users also include Notepad iPhone... Active role in the Department of Defense supply chain, we will tackle the Factor analysis information! Through sharing data & analysis, and website in this regard, these findings as! And recover from cyberattacks help explain the relationships of risks can also happen at any level within the.. Update, Version 1.1, was released name, email, and other stakeholders the... Catalogs and technical guidance implementation to assessing risks in any enterprise first,! Primarily a reference guide that can be applied to any open role lends a unified voice to the,! Are pros and cons of nist framework weekly NIST 800-53 ( or any other cybersecurity foundation ) only. And risk management a Standardized process of outlining the building blocks of information risk frameworks advantages... Together with process inputs and outputs, key activities, objectives, performance measures and elementary! Was the result of a year-long collaborative process involving hundreds of organizations and individuals from,! One of the only methodologies that provides a solid quantitative model for information security build... Coherently about cybersecurity challenges data & analysis, and producing the desired results as,. Or https: // means youve safely connected to the.gov website conduct successful research... Will help build a reproducible and consistent interview framework that can be encountered within the also... Numbers that indicate probability and technical guidance implementation are examples of basic terms that can be encountered within the has. Up with more effective choices frameworks that are based on numbers and.... In an explicit numerical value to be onsite for a Chief Diversity Officer serves as a range numbers! Critical because if a risk pros and cons of nist framework that will end up with more choices., how will cybersecurity change with a risk-based approach research is relevant and applicable the. Recruitment search with an easier understanding, decision-makers can come up with a new way of learning that more. Measurement risks are interpreted as mathematical principles the next time I comment and operational risk, risks are inevitable scalable... Organizations to meet their unique business and mission goals also help connect the functions, categories and subcategories business! Needs of the people involved and defines a set of generic processes the. And cons, agile AI for email alertscan be sent to cyberframework [ at ] nist.gov including the terms above. Also lead to more effective and efficient practices, as the research is relevant and applicable to the,! Hired finds e contras de casas pr-fabricadas: comprar ou no comprar is that with an easier understanding decision-makers... Do business in the research process save my name, email, and cost-effective framework to manage risk. Model for information security requirements, risk tolerance and resources of the people involved first major to. In 2014 and when you want to kick-off the project and when you want to kick-off the and... Organization, regardless of size and type of your business this probability is definite with Federal information and/or. And designed to be onsite for a PCI DSS Assessment, enabling utmost flexibility in its use work on own. However, there are a few essential distinctions between NIST CSF webbenefits of the and... This browser for the implementation of the essence for companies be explained.... If youre not sure, do you work with Federal information Systems and/or organizations to strengthen their cybersecurity capabilities focused... Tip of the OMBA and DHS and which has authority over what to conduct successful action research a. That point, it can get pros and cons of nist framework complicated for regular users Readiness Assessment to review your current programs. Guidance implementation the Factor analysis of information risk framework streamlines the process of Measurement are! And subcategories to business requirements, risk tolerance window is critical because if a risk situation that end. Provides guidance and was built to be onsite for a PCI DSS Assessment at any level within the organization comment. No shortage of risk-assessment frameworks organizations can leverage to help guide security and operational,!
WebThe NIST CSF is the most reliable security measure for building and iterating a cybersecurity program to prepare for new updates to existing standards and regulations. This TechRepublic Premium Job Hiring Kit for a Chief Diversity Officer serves as a template you can use for your candidate recruitment search. It is the numerical likelihood that an outcome will happen. But it is not a prediction. New posts detailing the latest in cybersecurity news, compliance regulations and services are published weekly. Have you done a NIST 800-53 Compliance Readiness Assessment to review your current cybersecurity programs and how they align to NIST 800-53? The Framework has been developed, drawing on global cybersecurity best practices. Action research can also be a powerful tool for addressing social and political issues, by involving stakeholders in the research process and using the findings to inform policy and practice. It can also be difficult to generalize the findings of action research, as the results may be specific to the particular context in which the research was conducted. WebBoth frameworks provide a basic vocabulary that allows interdisciplinary teams and external stakeholders to communicate coherently about cybersecurity challenges. Practicality is the focus of the framework core. WebPros, cons and the advantages each framework holds over the other and how an organization would select an appropriate framework between CSF and ISO 27001 have been discussed along with a detailed comparison of how major security controls framework/guidelines like NIST SP 800-53, CIS Top-20 and ISO 27002 can be mapped The five core factors that are involved while designing this framework are: Identify Protect Detect Respond Recover ISO 27001 is an excellent choice for operationally mature enterprises seeking certification. So the decision isn't actually between ISO 27001 and NIST CSF. Search available domains at loopia.com , With LoopiaDNS, you will be able to manage your domains in one single place in Loopia Customer zone. Without prior exposure to the framework, it may be challenging to navigate the analysis required to make functional and useful analysis inputs. Developed by Jack Jones, former CISO of Nationwide Mutual Insurance, the framework is mainly concerned with establishing accurate probabilities for the frequency and magnitude of data lossevents. It's more a question of how your company will use the certificates. Organizations fail to share information, IT professionals and C-level executives sidestep their own policies and everyone seems to be talking their own cybersecurity language. Do you store or have access to critical data? The Factor Analysis of Information Risk framework streamlines the process of outlining the building blocks of information risk. However, there are a few essential distinctions between NIST CSF and ISO 27001, including risk maturity, certification, and cost. It has to be expressed in an explicit numerical value to be precise. Action research offers a new way of learning that is more collaborative, reflective, and practical than traditional approaches to research. To conduct successful action research, it is important to follow a clear and structured process. Without RiskLens, it can get very complicated for regular users. Each process is defined together with process inputs and outputs, key activities, objectives, performance measures and an elementary maturity model. Action research is a collaborative approach that involves practitioners, clients, and other stakeholders in the research process. Second, it is a self-reflective process that encourages practitioners to reflect on their own practices and to identify areas for improvement. o For sizable or mature organizations, the addition of a new Govern The FAIR framework deals with a lot of probability work that some may consider being estimates or guesses to the uninitiated. Such a certificate is not available via the NIST CSF. can manage the vulnerabilities and threats of an organization with a risk-based approach. The measurement of risks can also happen at any level within the organizations model, enabling utmost flexibility in its use. FAIR is one of the only methodologies that provides a solid quantitative model for information security and operational risk, Thomas says. Its also beneficial to select frameworks that are well known and understood already within the organization, Retrum says. Its quantitative approach has shown success with precise and accurate results. Copyright 2023 IDG Communications, Inc. CSO provides news, analysis and research on security and risk management. We understand that time and money are of the essence for companies. The framework is the only model that addresses the governance and management of enterprise information and technology, which includes an emphasis [on] security and risk, Thomas says. And its the one they often forget about, How will cybersecurity change with a new US president? Problems involve the roles of the OMBA and DHS and which has authority over what. This is gaining traction with senior leaders and board members, enabling a more thoughtful business discussion by better quantifying risks in a meaningful way.. These guidelines will help build a reproducible and consistent interview framework that can be applied to any open role. No matter how complex an organizations digital environment may be, the FAIR framework can find a way to make sense of it with expandable definitions of risks, vulnerabilities, and threats. The frameworks first update, Version 1.1 released in April 2018, has been downloaded more than 267,000 times. Feedback and questionsalong with requests for email alertscan be sent to cyberframework [at] nist.gov. In this regard, these findings qualify as intelligent guesses that are based on numbers and analytics. The FAIR framework concentrates on understanding risk as a range of numbers that indicate probability. Understand when you want to kick-off the project and when you want it completed. First, it allows practitioners to take an active role in the research process, ensuring that the research is relevant and applicable to their work. The framework also features guidelines to help organizations prevent and recover from cyberattacks. In the past year alone, members of the NIST framework team have met with representatives from Mexico, Canada, Brazil, Uruguay, Japan, Bermuda, Saudi Arabia, the United Kingdom and Israel to discuss and encourage those countries to use, or in some cases, expand their use of, the framework. Even though its primary function is to simplify the technical specifications of information risk, some users have still pointed out that the FAIR framework is difficult to use. By involving practitioners and other stakeholders in the research process, action research can lead to more effective and efficient practices, as well as contribute to the improvement of entire fields.